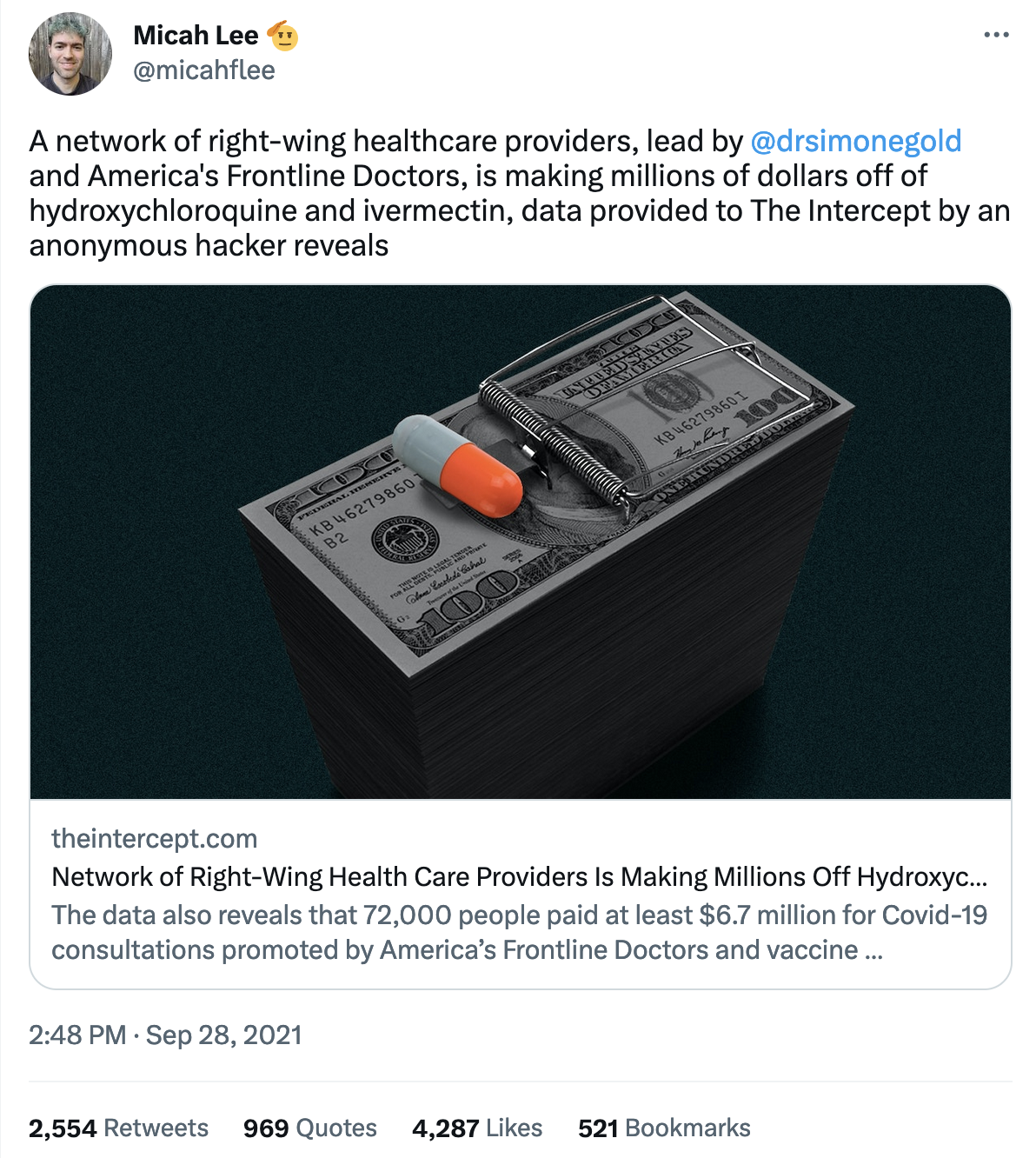
Twitter Thread: Healthcare network led by Simone Gold and America's Frontline Doctors making millions off hydroxychloroquine and ivermectin
An archived Twitter thread from September 28, 2021
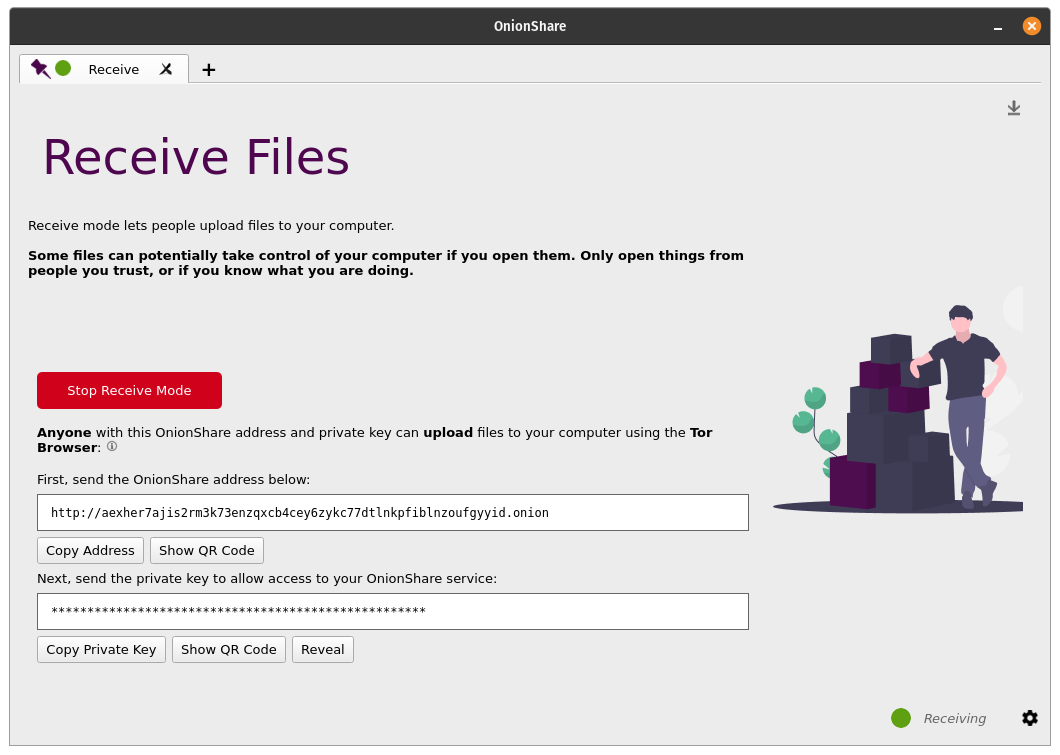
Goodbye, passwords in OnionShare
I'm excited to announce that OnionShare 2.4 is now out and the major change in this version is that we've completely gotten rid of passwords! Private OnionShare services are now protected using private keys (aka client authentication) on the Tor layer instead of instead of basic authentication on the HTTP layer. Check out the new version at onionshare.org!
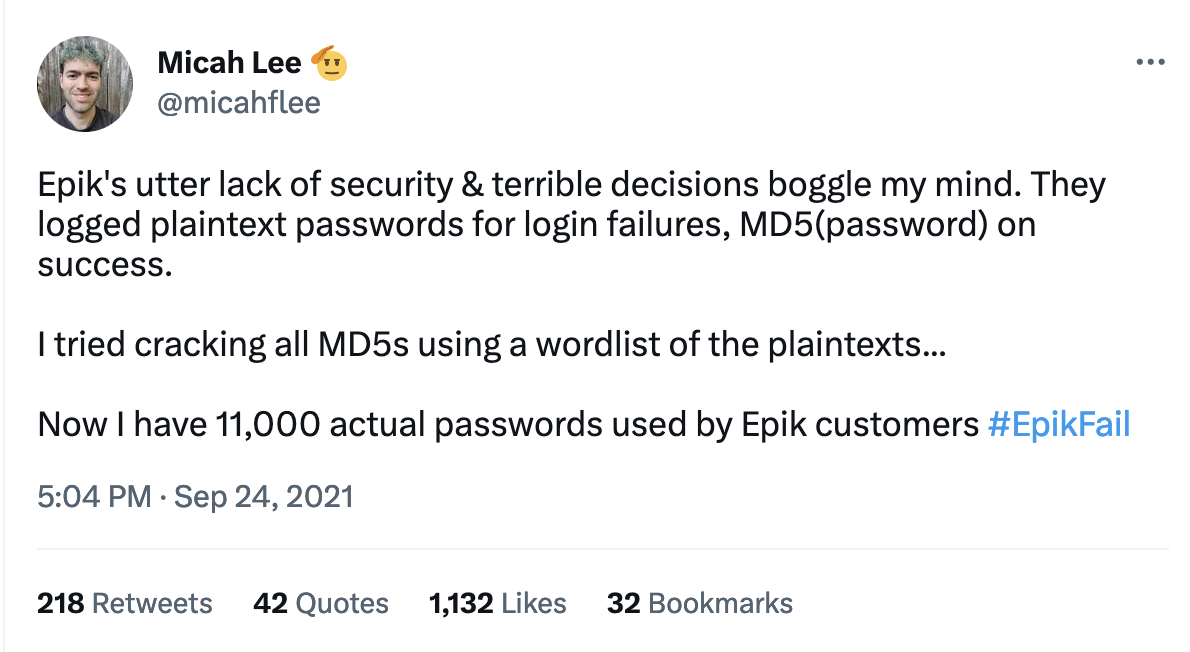
Twitter Thread: Epik's utter lack of security & terrible decisions boggle my mind
An archived Twitter thread from September 24, 2021
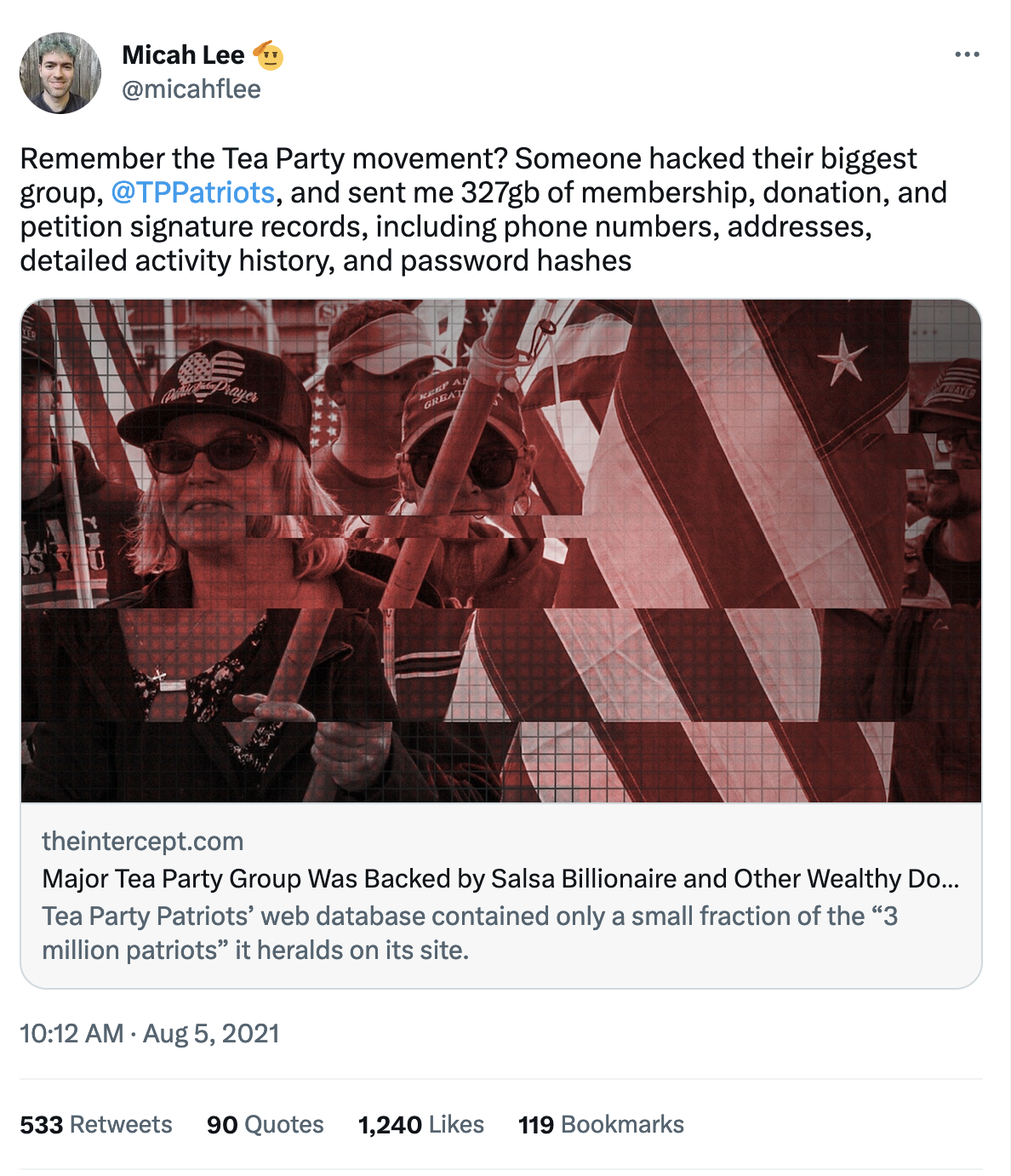
Twitter Thread: 327GB of membership, donation, and petition signature records from the Tea Party Patriots
An archived Twitter thread from August 5, 2021
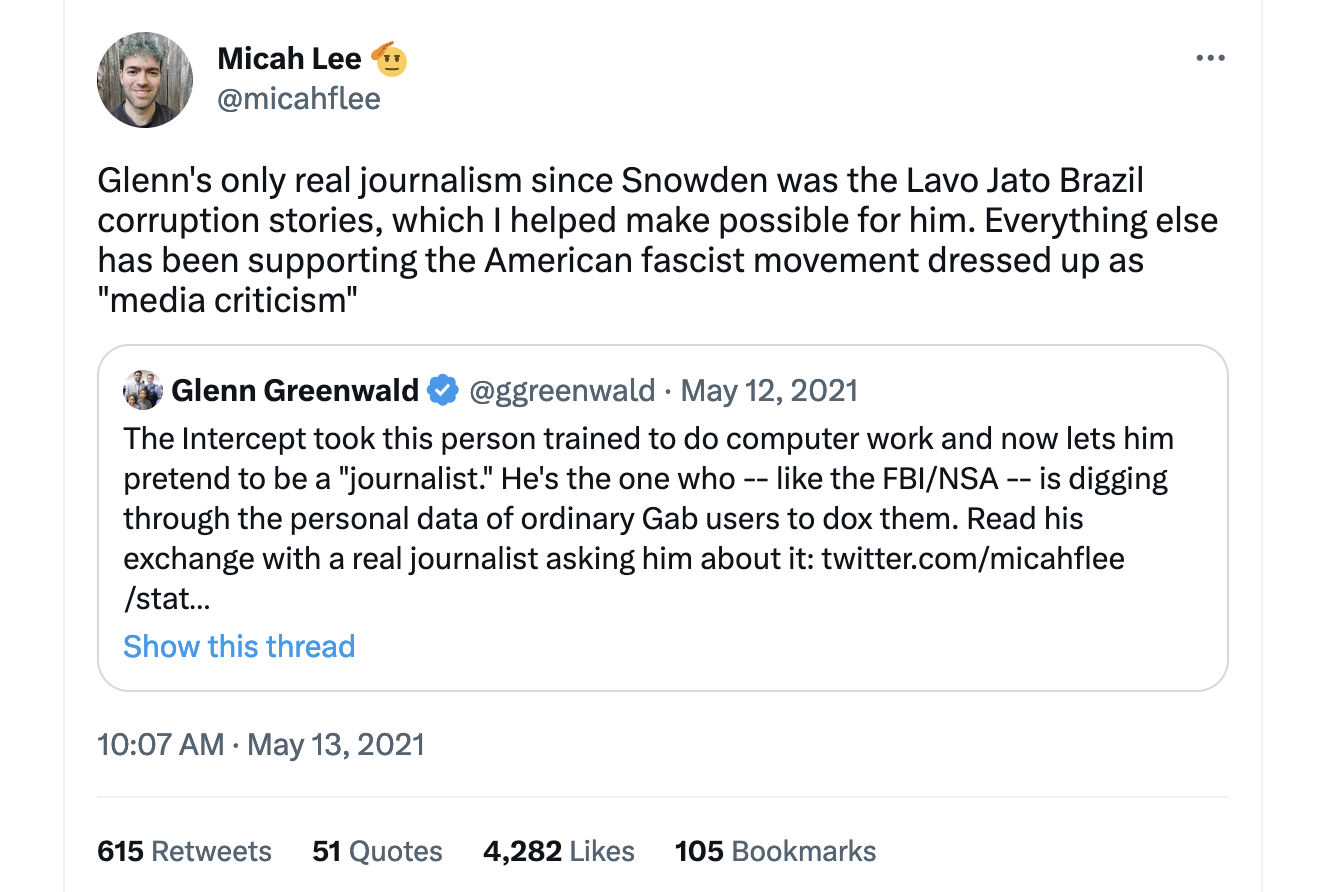
Twitter Thread: Glenn Greenwald supporting the American fascist movement dressed up as "media criticism"
An archived Twitter thread from May 13, 2021
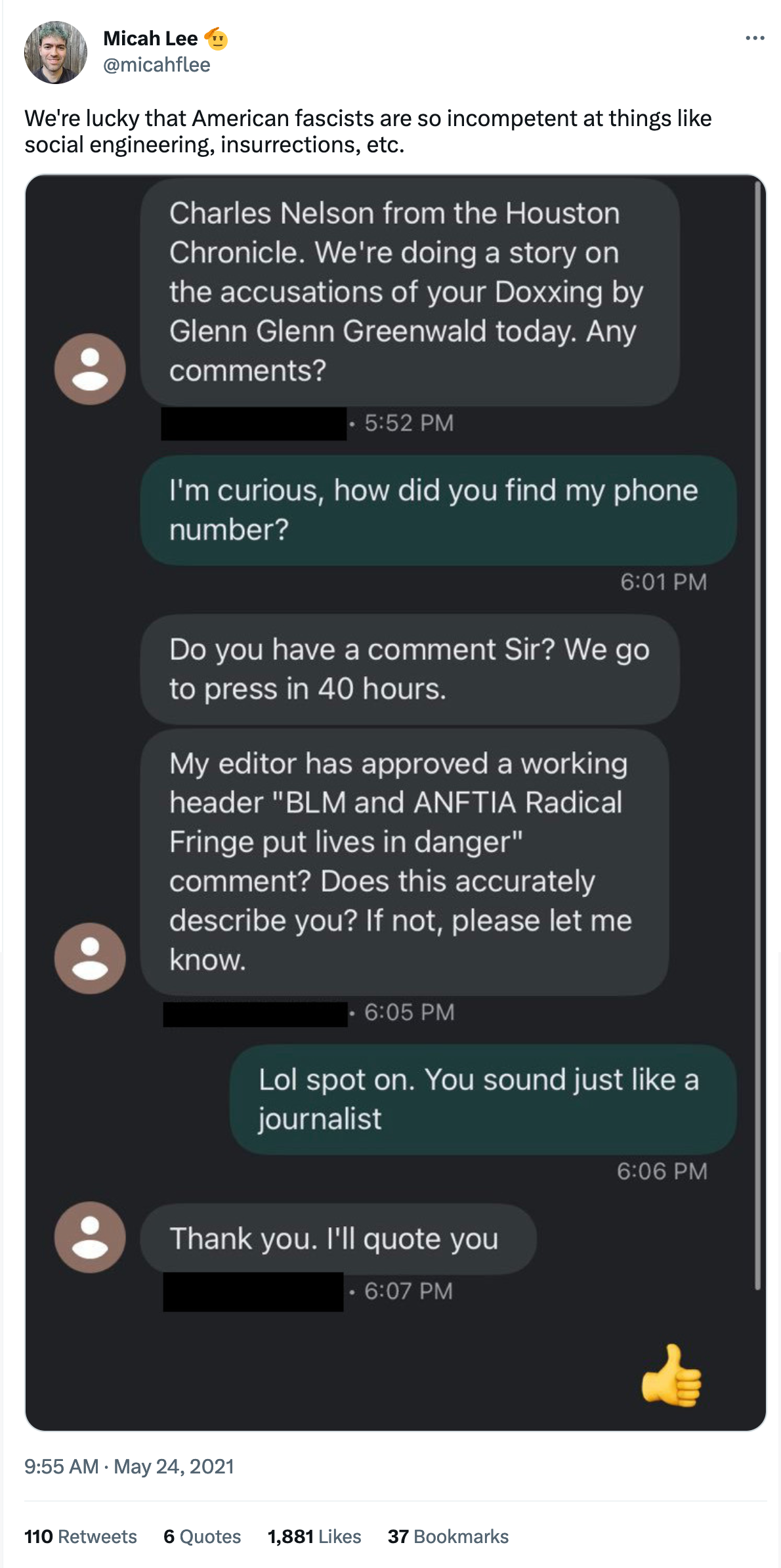
Twitter Thread: Glenn Greenwald-related social engineering/death threats
An archived Twitter thread from May 4, 2021
Running an OnionShare anonymous dropbox on a Raspberry Pi
Now that the command line version of OnionShare has better support for running on headless Linux servers, I figured I should set up a dedicated Raspberry Pi anonymous dropbox server, and while I'm at it document how I'm doing it in a blog post.
OnionShare 2.3 adds tabs, anonymous chat, better command line support, and quite a bit more
After a ridiculously long sixteen months (or roughly ten years in pandemic time) I'm excited to announce that OnionShare 2.3 is out! Download it from onionshare.org.
This version includes loads of new and exciting features which you can read about in much more detail on the brand new OnionShare documentation website, docs.onionshare.org. For now though I'm just going to go over the major ones: tabs, anonymous chat, and better command line support.
Easily automate deleting your old tweets, likes, and DMs with Semiphemeral
Roughly one hundred years ago, in June of 2019, I released an open source Twitter privacy tool called Semiphemeral that makes it simple-ish to delete years of old tweets. The great thing about Semiphemeral is, unlike similar tools, it's flexible: you don't have to delete all of your old tweets if you don't want to. You can, say, choose to keep tweets that have at least 20 likes, flag specific tweets you want to never delete, or delete all your retweets and likes that are older than a week.
But at the time, Semiphemeral was only usable by the nerdiest among us. It required running commands in a terminal window, creating your own Twitter API key, and, if you want to automate it, setting up a cron job on a server. But this is no longer the case!
For the last several months I've been running an easy-to-use hosted version at Semiphemeral.com. Now anyone* can easily delete their old tweets, likes, and now even direct messages (more on this below).
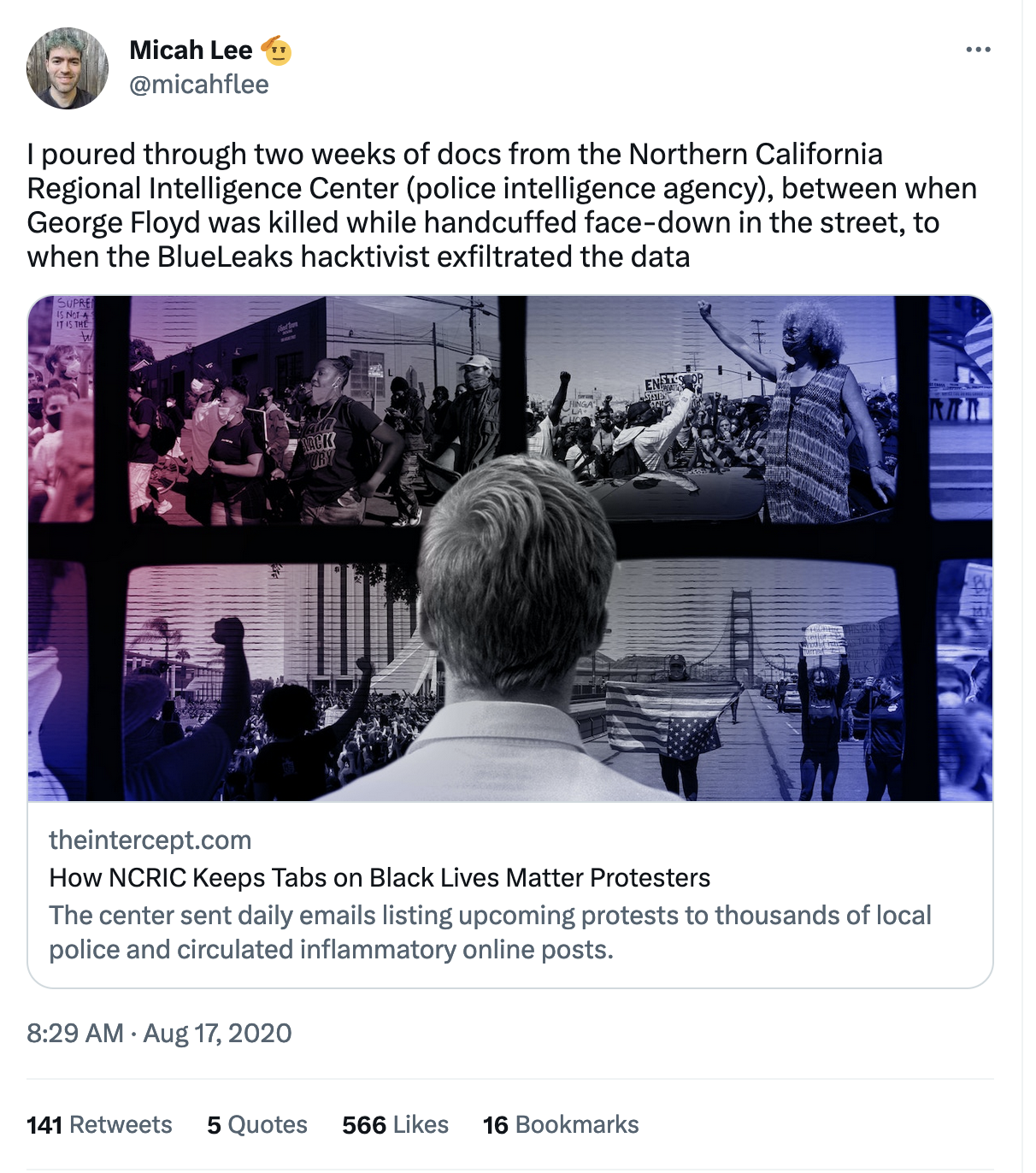
Twitter Thread: Northern California Regional Intelligence Center
An archived Twitter thread from August 17, 2020






 Subscribe to feed
Subscribe to feed