Elon banned me from Twitter for doing journalism. Good riddance.
It's been nearly six months since Elon Musk threw one of his first tantrums as the King of Twitter and banned me (along with a bunch of other journalists) for tweeting about him censoring Mastodon. A few days later he "reinstated" my account but I was still locked out until I agreed to delete my forbidden tweet that the billionaire didn't like. And I've been locked out ever since.
Capturing the Flag with GPT-4
This weekend I went to BSides SF 2023 and had a blast. I went to some really interesting talks (including an excellent one about adversarial machine learning), but mostly I spent my time solving CTF hacking challenges. And this time, I did it with the help of GPT-4, the latest generation of OpenAI's ChatGPT generative language model. GPT-4 straight up solved some challenges for me, which blew my mind. There were definitely several flags I got that I wouldn't have gotten without the help of GPT-4. For challenges that GPT-4 didn't solve on its own, it provided incredibly helpful tips, or quickly wrote scripts that would have been tedious or time consuming for me to write myself. Good thing there's (almost) no such thing as cheating in CTF!
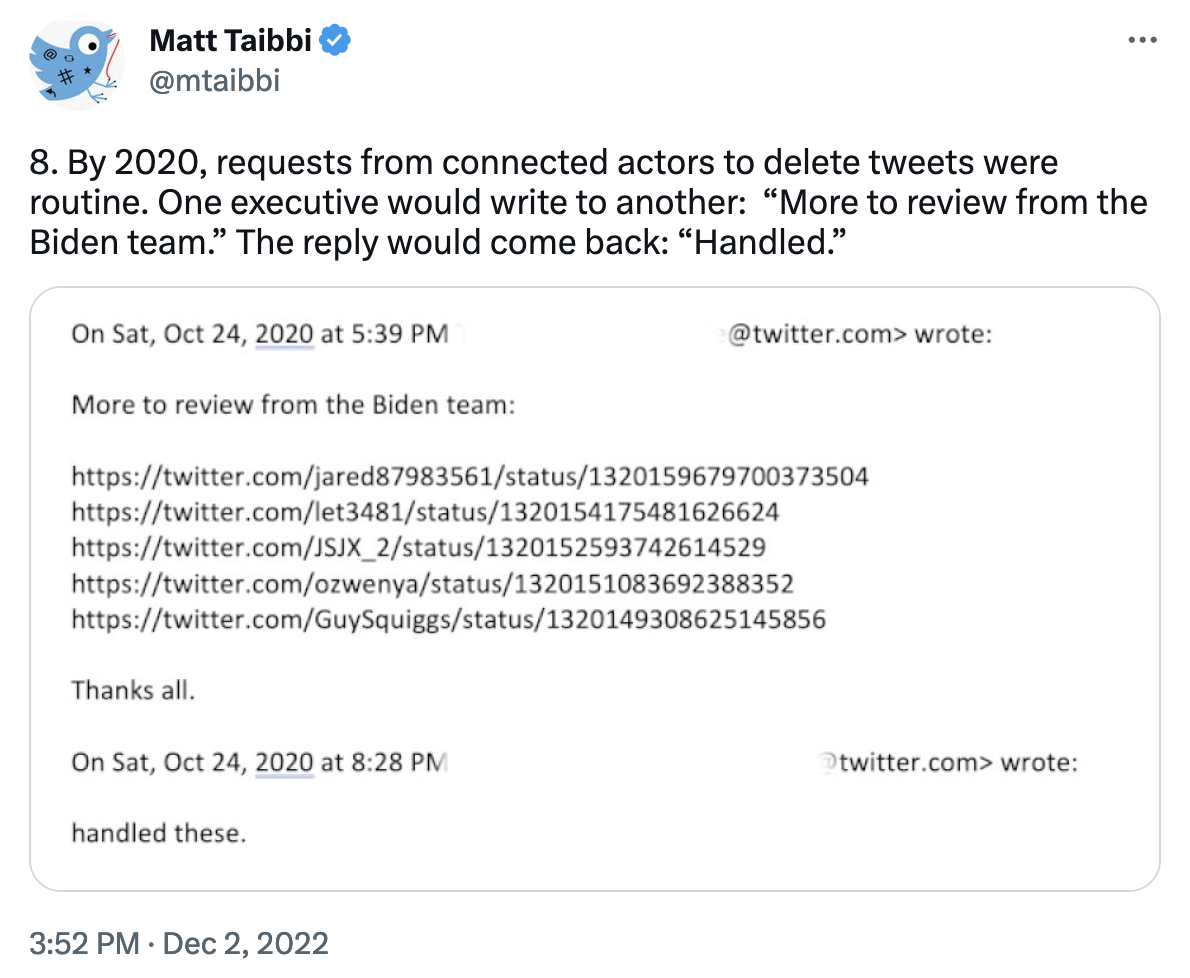
Twitter Thread: Response to Matt Taibbi's first Twitter Files Tweets
An archived Twitter thread from December 2, 2022
OnionShare 2.6 has a quickstart screen, automatic censorship circumvention, and better packaging
I'm excited to announce that the OnionShare team just released version 2.6! You can download it from onionshare.org. Here are the main things that are new.
Stories about Peter Eckersley
My friend Peter Eckersley tragically and unexpectedly died on Friday. I hadn't spent much time with him in the last few years, but I wish that I had because he had such a big impact on my life. Wikipedians have created an article about Peter, and Seth Schoen, who worked closely with me and Peter at EFF on the tech team, wrote a memorial for him on the Let's Encrypt forum. I thought I would share a few stories about Peter here.
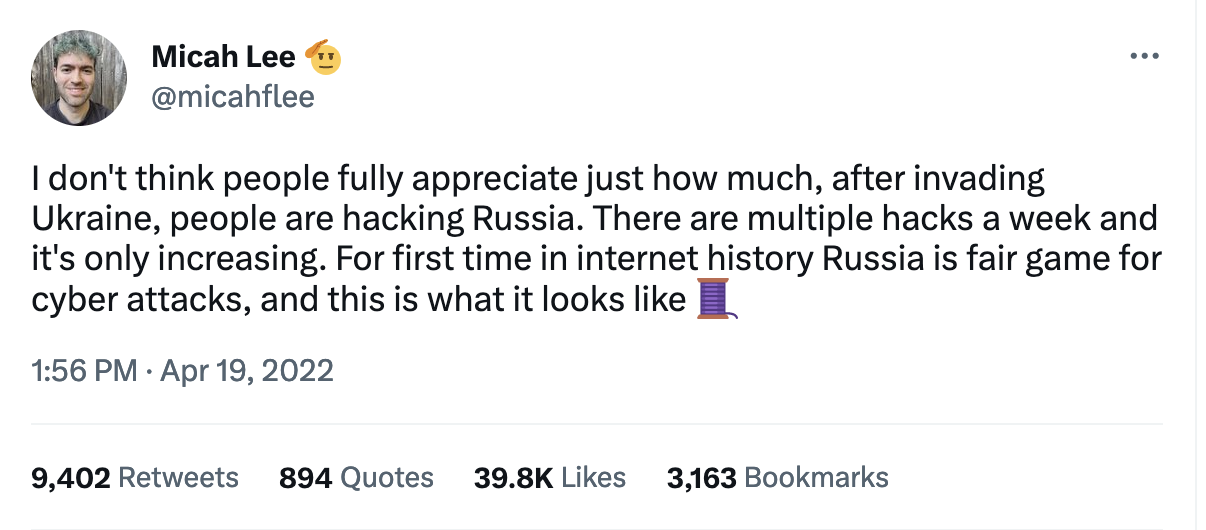
Twitter Thread: For first time in internet history Russia is fair game for cyber attacks, and this is what it looks like
An archived Twitter thread from April 19, 2022
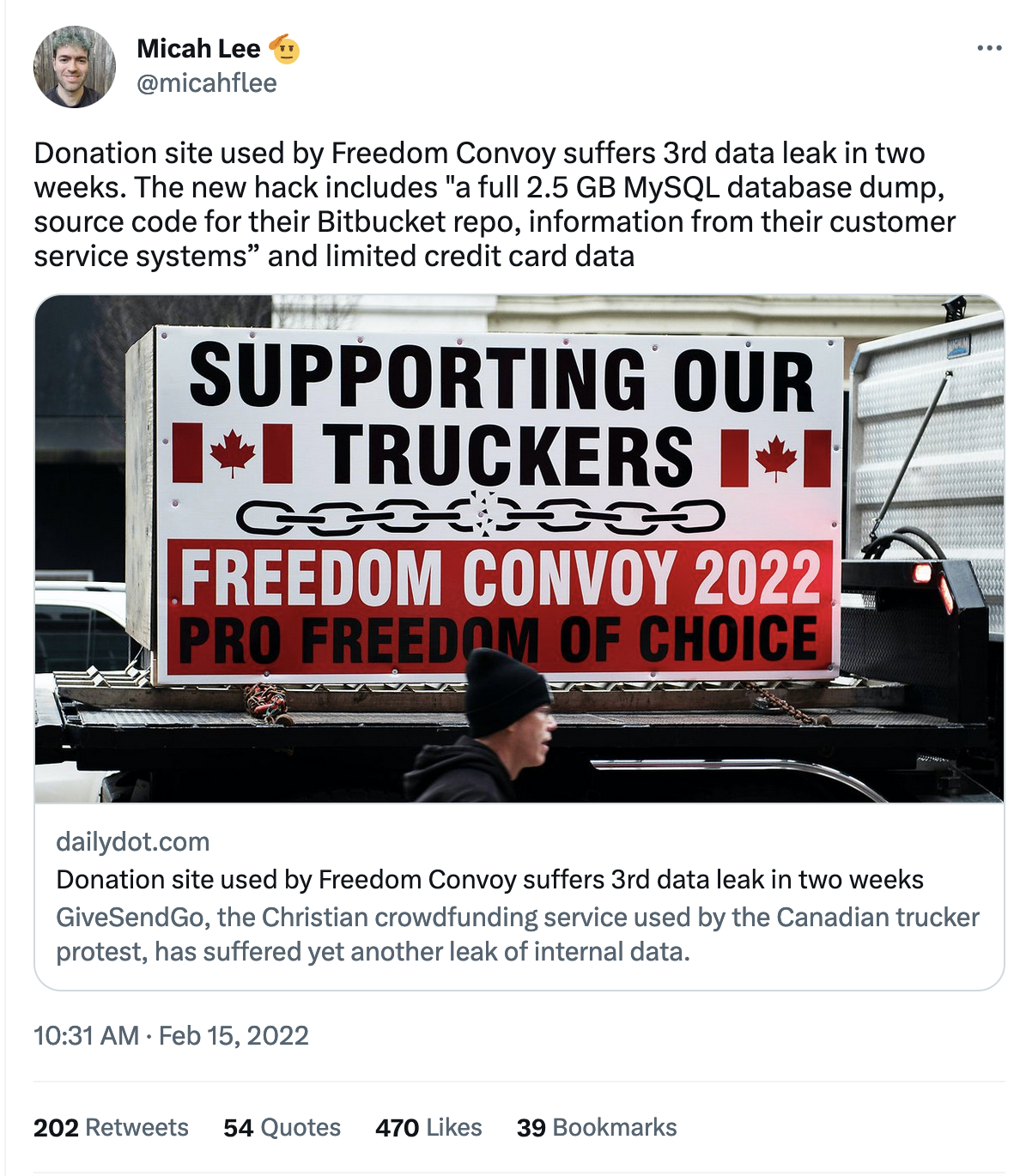
Twitter Thread: "Freedom Convoy" and the GiveSendGo hacks
An archived Twitter thread from February 15, 2022
OnionShare 2.5 fixes security issues and adds censorship circumvention features
The OnionShare team has just released OnionShare 2.5! This version fixes security vulnerabilities uncovered in our first comprehensive security audit, and also includes improved censorship circumvention features. Download it from onionshare.org.
Qube Apps: a Flatpak-based app store for each qube
I really like Qubes but I haven't been using it a lot lately. I have a Qubes laptop that I use for specific high security tasks, but my daily driver the last few months has been Ubuntu or Pop!_OS (I really like the tiling windows and the design), and sometimes macOS. Qubes is great, but it can be cumbersome to use.
Twitter Thread: Healthcare network led by Simone Gold and America's Frontline Doctors making millions off hydroxychloroquine and ivermectin
An archived Twitter thread from September 28, 2021








 Subscribe to feed
Subscribe to feed