Running an OnionShare anonymous dropbox on a Raspberry Pi

Now that the command line version of OnionShare has better support for running on headless Linux servers, I figured I should set up a dedicated Raspberry Pi anonymous dropbox server, and while I'm at it document how I'm doing it in a blog post.
Find a Raspberry Pi
Personally, I dug through my cardboard box full of random electronics and pulled out a trusty old Raspberry Pi 3 Model B. After all, who among us doesn't have extra Raspberry Pis laying around in piles of old electronics? If you're not as fortunate as I, at the time of writing the fanciest model is the Raspberry Pi 4 Model B, and it costs $35.
Raspberry Pis use microSD cards as their hard drive, so you'll also need a microSD card reader that you can plug into your computer to set it up, a micro-USB cable to provide power to your Pi, and an internet connection (ethernet is simplest, but wifi works too).
Install Ubuntu Server 20.04 on the Pi
Follow this tutorial that Ubuntu makes to install Ubuntu on your Pi -- that's what I'm doing. I'm using the Ubuntu Server 20.04.2 LTS (RPi 3/4/400) 64-bit image. Once you get to the step "4. Boot Ubuntu Server" you can come back here.
I don't feel like plugging an HDMI cable and USB keyboard into my Pi, so after plugging in ethernet and power, I'm going to need to discover my Pi's IP address so I can connect to it remotely over the network. I'm using nmap to do this. You can install it from your Linux package manager, from Homebrew on a Mac, or from nmap's website on Windows)
Because my local network IP address is 192.168.1.x, I'm going to scan my whole subnet (192.168.1.0/24) for computers with the SSH port (22) open, and one of them is bound to be my Pi:
$ nmap -p22 --open 192.168.1.0/24
Starting Nmap 7.91 ( https://nmap.org ) at 2021-02-23 17:51 PST
Nmap scan report for 192.168.1.46
Host is up (0.0015s latency).
PORT STATE SERVICE
22/tcp open ssh
Nmap done: 256 IP addresses (7 hosts up) scanned in 3.13 seconds
There it is, my Pi's IP address is 192.168.1.46. So let's see if I can SSH into it. If you're following along, make sure to use the IP of your Pi, as it's probably different than mine. The default username and password are both ubuntu.
$ ssh ubuntu@192.168.1.46
The authenticity of host '192.168.1.46 (192.168.1.46)' can't be established.
ECDSA key fingerprint is SHA256:tdB9dxpe4dIpFfvbjNdPpPVLeBlpTXaSu6SCaabjyFc.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.1.46' (ECDSA) to the list of known hosts.
ubuntu@192.168.1.46's password:
You are required to change your password immediately (administrator enforced)
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-1028-raspi aarch64)
[...snip...]Accept the fingerprint. After logging in, you're forced to reset the password. Set it to something random and save it in your password manager. You do use a password manager, right?
After you reset your password, your connection will close and you'll need to SSH in again:
[...snip...]
WARNING: Your password has expired.
You must change your password now and login again!
Changing password for ubuntu.
Current password:
New password:
Retype new password:
passwd: password updated successfully
Connection to 192.168.1.46 closed.
$ ssh ubuntu@192.168.1.46
ubuntu@192.168.1.46's password:
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-1028-raspi aarch64)
[...snip...]
ubuntu@ubuntu:~$ (hacker voice) I'm in.
Go ahead and install updates by running:
sudo apt update
sudo apt upgrade -y
Install OnionShare
OnionShare is written in python, and you can install the command line version use python's package manager pip. So first, I must install pip:
sudo apt install python3-pipNow I'm going to install OnionShare itself:
pip3 install --user onionshare-cliWhen you install programs with pip and use the --user flag, it installs them into ~/.local/bin, which isn't in your path by default. This will add ~/.local/bin to your path automatically for the next time you SSH into your Pi:
echo "PATH=\$PATH:~/.local/bin" >> ~/.bashrc
source ~/.bashrc
Okay, now try running onionshare-cli. You should see the usage information:
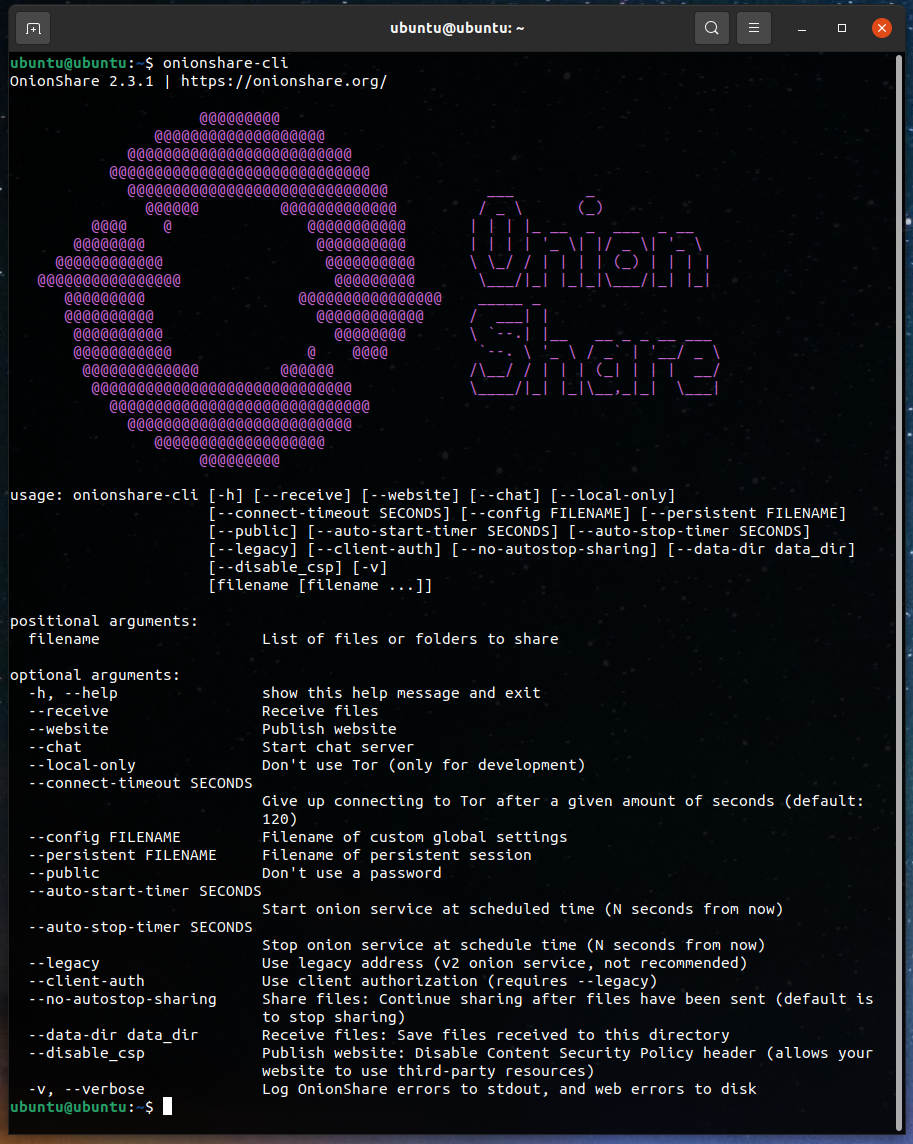
Test it out (install tor)
Great, so let's start by seeing if we can run a chat server:
$ onionshare-cli --chat
OnionShare 2.3.1 | https://onionshare.org/
@@@@@@@@@
@@@@@@@@@@@@@@@@@@@
@@@@@@@@@@@@@@@@@@@@@@@@@
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ ___ _
@@@@@@ @@@@@@@@@@@@@ / _ \ (_)
@@@@ @ @@@@@@@@@@@ | | | |_ __ _ ___ _ __
@@@@@@@@ @@@@@@@@@@ | | | | '_ \| |/ _ \| '_ \
@@@@@@@@@@@@ @@@@@@@@@@ \ \_/ / | | | | (_) | | | |
@@@@@@@@@@@@@@@@ @@@@@@@@@ \___/|_| |_|_|\___/|_| |_|
@@@@@@@@@ @@@@@@@@@@@@@@@@ _____ _
@@@@@@@@@@ @@@@@@@@@@@@ / ___| |
@@@@@@@@@@ @@@@@@@@ \ `--.| |__ __ _ _ __ ___
@@@@@@@@@@@ @ @@@@ `--. \ '_ \ / _` | '__/ _ \
@@@@@@@@@@@@@ @@@@@@ /\__/ / | | | (_| | | | __/
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ \____/|_| |_|\__,_|_| \___|
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@@@@@@@@@@@@@@@@@@@@@@@@@
@@@@@@@@@@@@@@@@@@@
@@@@@@@@@
You must install tor to use OnionShare from the command lineOh right, I need to install tor. That's easy:
sudo apt install torOkay, let's try again:
$ onionshare-cli --chat
OnionShare 2.3.1 | https://onionshare.org/
@@@@@@@@@
@@@@@@@@@@@@@@@@@@@
@@@@@@@@@@@@@@@@@@@@@@@@@
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ ___ _
@@@@@@ @@@@@@@@@@@@@ / _ \ (_)
@@@@ @ @@@@@@@@@@@ | | | |_ __ _ ___ _ __
@@@@@@@@ @@@@@@@@@@ | | | | '_ \| |/ _ \| '_ \
@@@@@@@@@@@@ @@@@@@@@@@ \ \_/ / | | | | (_) | | | |
@@@@@@@@@@@@@@@@ @@@@@@@@@ \___/|_| |_|_|\___/|_| |_|
@@@@@@@@@ @@@@@@@@@@@@@@@@ _____ _
@@@@@@@@@@ @@@@@@@@@@@@ / ___| |
@@@@@@@@@@ @@@@@@@@ \ `--.| |__ __ _ _ __ ___
@@@@@@@@@@@ @ @@@@ `--. \ '_ \ / _` | '__/ _ \
@@@@@@@@@@@@@ @@@@@@ /\__/ / | | | (_| | | | __/
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ \____/|_| |_|\__,_|_| \___|
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@@@@@@@@@@@@@@@@@@@@@@@@@
@@@@@@@@@@@@@@@@@@@
@@@@@@@@@
Connecting to the Tor network: 100% - Done
Give this address to the recipient:
http://onionshare:appetizer-acid@hhzxxzfsx34ckxjtl3z6cjgfk73tyr3fxbsu3rumiqsgdz6nvmorhnyd.onion
Press Ctrl+C to stop the serverLoad the OnionShare address you see in Tor Browser to make sure it works.
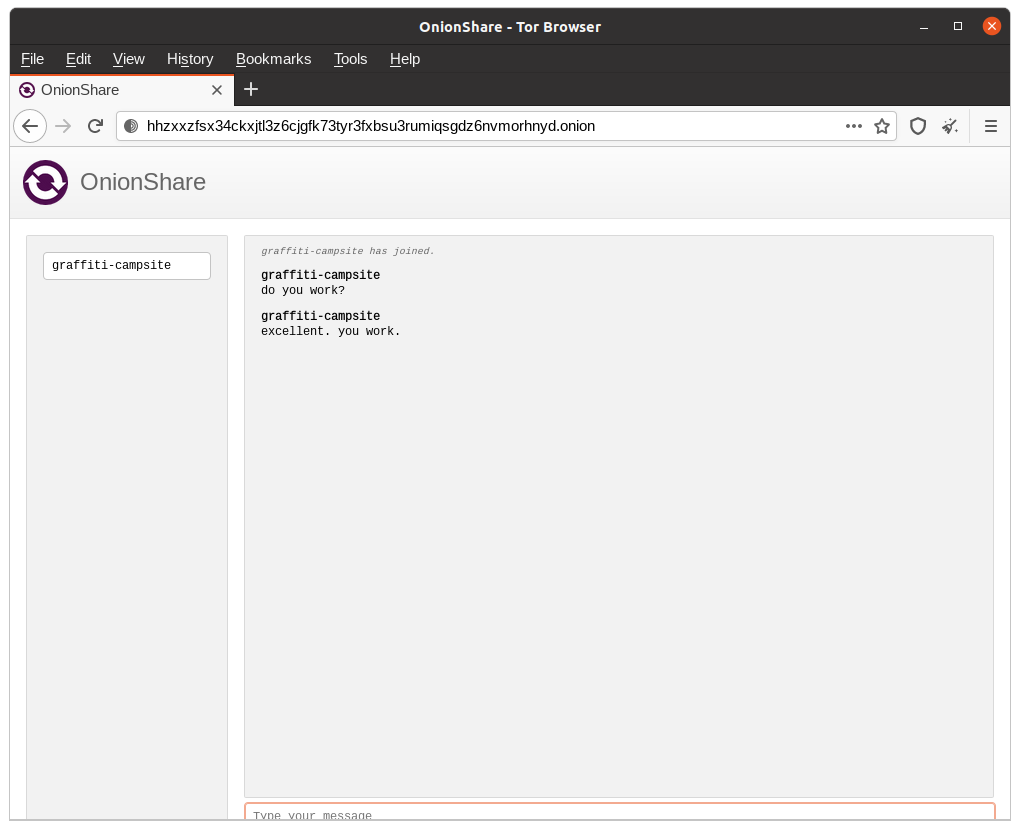
Great.
Press Ctrl-C to quit OnionShare.
Start a persistent anonymous dropbox
To let people anonymously upload files to your computer (in this case, your Raspberry Pi) you use receive mode. In the command line this is the --receive flag.
You'll also want to make sure you use --persistent. This will save the Tor onion key into a file so that if you ever, for example, reboot your Raspberry Pi, you can start up your service with the exact same OnionShare address.
You'll also probably want to use --public which disables the default password protection. Basically, this lets you post a link to your anonymous dropbox on Twitter (for example) and anyone can go there to anonymously leak documents to you.
Putting it all together:
$ onionshare-cli --receive --persistent ~/anon-dropbox.session --public
OnionShare 2.3.1 | https://onionshare.org/
@@@@@@@@@
@@@@@@@@@@@@@@@@@@@
@@@@@@@@@@@@@@@@@@@@@@@@@
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ ___ _
@@@@@@ @@@@@@@@@@@@@ / _ \ (_)
@@@@ @ @@@@@@@@@@@ | | | |_ __ _ ___ _ __
@@@@@@@@ @@@@@@@@@@ | | | | '_ \| |/ _ \| '_ \
@@@@@@@@@@@@ @@@@@@@@@@ \ \_/ / | | | | (_) | | | |
@@@@@@@@@@@@@@@@ @@@@@@@@@ \___/|_| |_|_|\___/|_| |_|
@@@@@@@@@ @@@@@@@@@@@@@@@@ _____ _
@@@@@@@@@@ @@@@@@@@@@@@ / ___| |
@@@@@@@@@@ @@@@@@@@ \ `--.| |__ __ _ _ __ ___
@@@@@@@@@@@ @ @@@@ `--. \ '_ \ / _` | '__/ _ \
@@@@@@@@@@@@@ @@@@@@ /\__/ / | | | (_| | | | __/
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ \____/|_| |_|\__,_|_| \___|
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@@@@@@@@@@@@@@@@@@@@@@@@@
@@@@@@@@@@@@@@@@@@@
@@@@@@@@@
Connecting to the Tor network: 100% - Done
* Running on http://127.0.0.1:17636/ (Press CTRL+C to quit)
Files sent to you appear in this folder: /home/ubuntu/OnionShare
Warning: Receive mode lets people upload files to your computer. Some files can potentially take control of your computer if you open them. Only open things from people you trust, or if you know what you are doing.
Give this address to the sender:
http://vxat6yszh7o5r2fxzvibxsb4lmfi6yzudobn3o3yz2vhvue3z2xmbqid.onion
Press Ctrl+C to stop the serverNow, load the OnionShare address in Tor Browser to make sure it works.
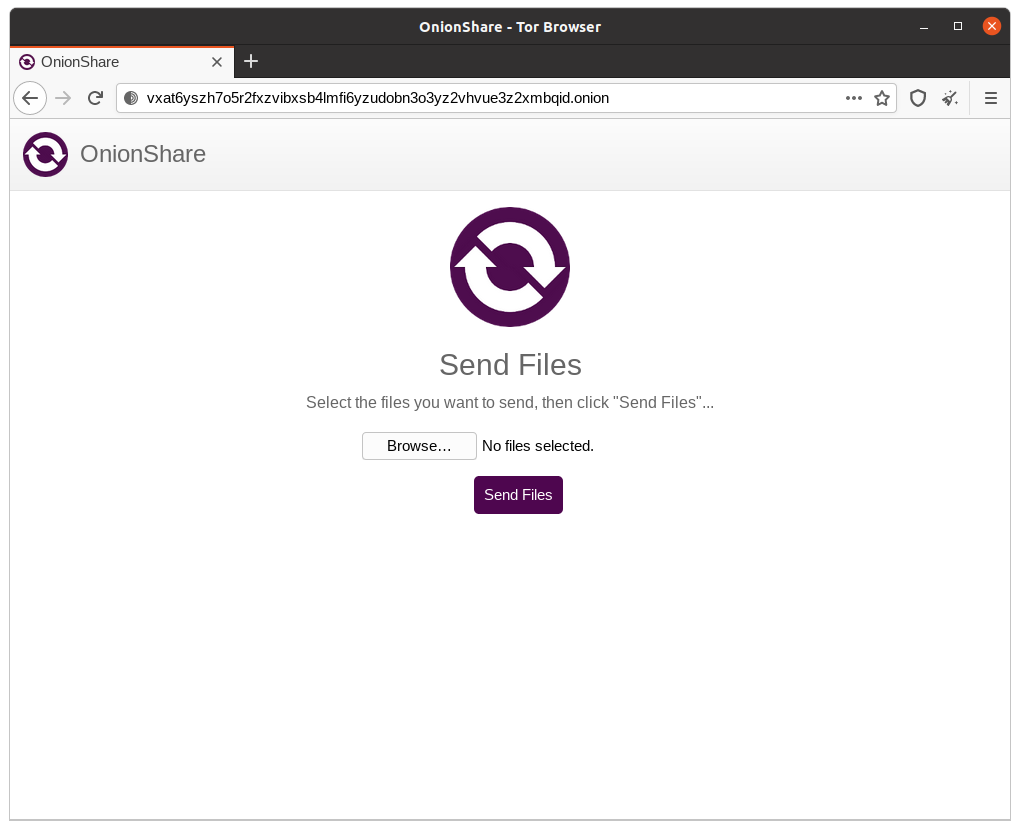
It works!
And live web logs get displayed in the terminal as well. For example when I loaded the OnionShare address, this was displayed in the terminal:
127.0.0.1 - - [24/Feb/2021 02:36:06] "GET / HTTP/1.1" 200 -
127.0.0.1 - - [24/Feb/2021 02:36:07] "GET /static_nwr7jepc7gzurz2tyf2ddqnaxe/css/style.css HTTP/1.1" 200 -
127.0.0.1 - - [24/Feb/2021 02:36:08] "GET /static_nwr7jepc7gzurz2tyf2ddqnaxe/js/jquery-3.5.1.min.js HTTP/1.1" 200 -
127.0.0.1 - - [24/Feb/2021 02:36:08] "GET /static_nwr7jepc7gzurz2tyf2ddqnaxe/js/receive.js HTTP/1.1" 200 -
127.0.0.1 - - [24/Feb/2021 02:36:08] "GET /static_nwr7jepc7gzurz2tyf2ddqnaxe/img/logo.png HTTP/1.1" 200 -
127.0.0.1 - - [24/Feb/2021 02:36:08] "GET /static_nwr7jepc7gzurz2tyf2ddqnaxe/img/logo_large.png HTTP/1.1" 200 -
127.0.0.1 - - [24/Feb/2021 02:36:09] "GET /static_nwr7jepc7gzurz2tyf2ddqnaxe/img/favicon.ico HTTP/1.1" 200 -You'll never get to know the IP addresses of people who visit your onion site. Their IP will always look like 127.0.0.1. This is how Tor onion services work: you run a service anonymously, and all the clients that connect to your service are anonymous as well. If someone loads your anonymous dropbox while you happen to be looking at the terminal, you'll be able to tell that someone is there because you'll see the logs they generate, but you won't know who it is.
Upload a file, and then see what was uploaded
Now, let's try uploading a file. In my case, I'm uploading a ~2.6mb file called IMG_0417.jpg.
In the terminal you can see the progress of the file as it uploads, and then you can see the location it was saved to:
=> 2.5 MiB IMG_0417.jpg
Received: /home/ubuntu/OnionShare/2021-02-24/22.29.20/IMG_0417.jpg
127.0.0.1 - - [24/Feb/2021 22:29:29] "POST /upload-ajax HTTP/1.1" 200 -
But now, how do I actually access this file? There are many ways. Here are some options:
In macOS or Windows
If you use macOS or Windows you can use SFTP software like Cyberduck. For example, here I'm setting up a new connection in Cyberduck called onionsharepi:
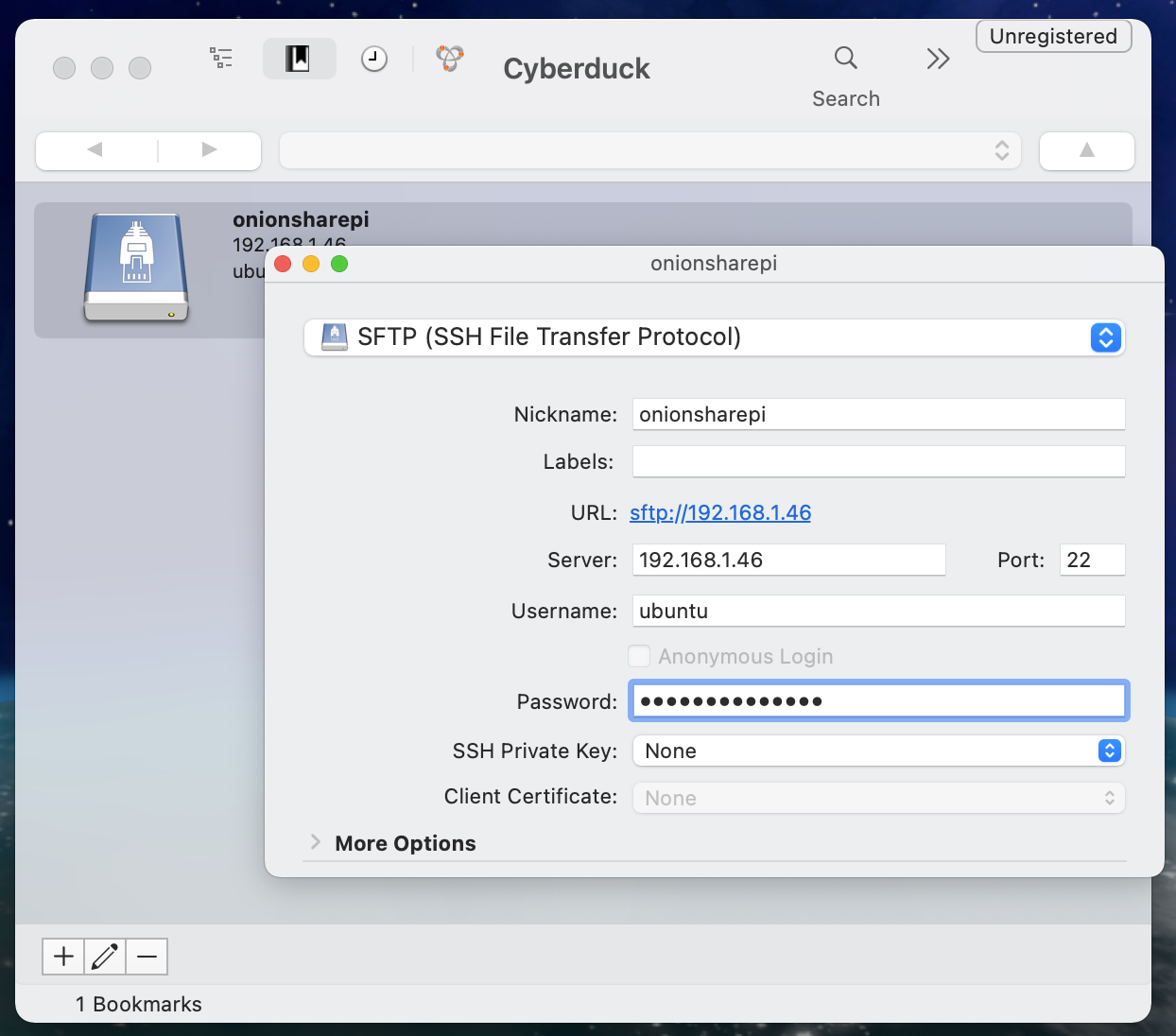
Then when I connect to it, I can browse the files and download anything to my computer:
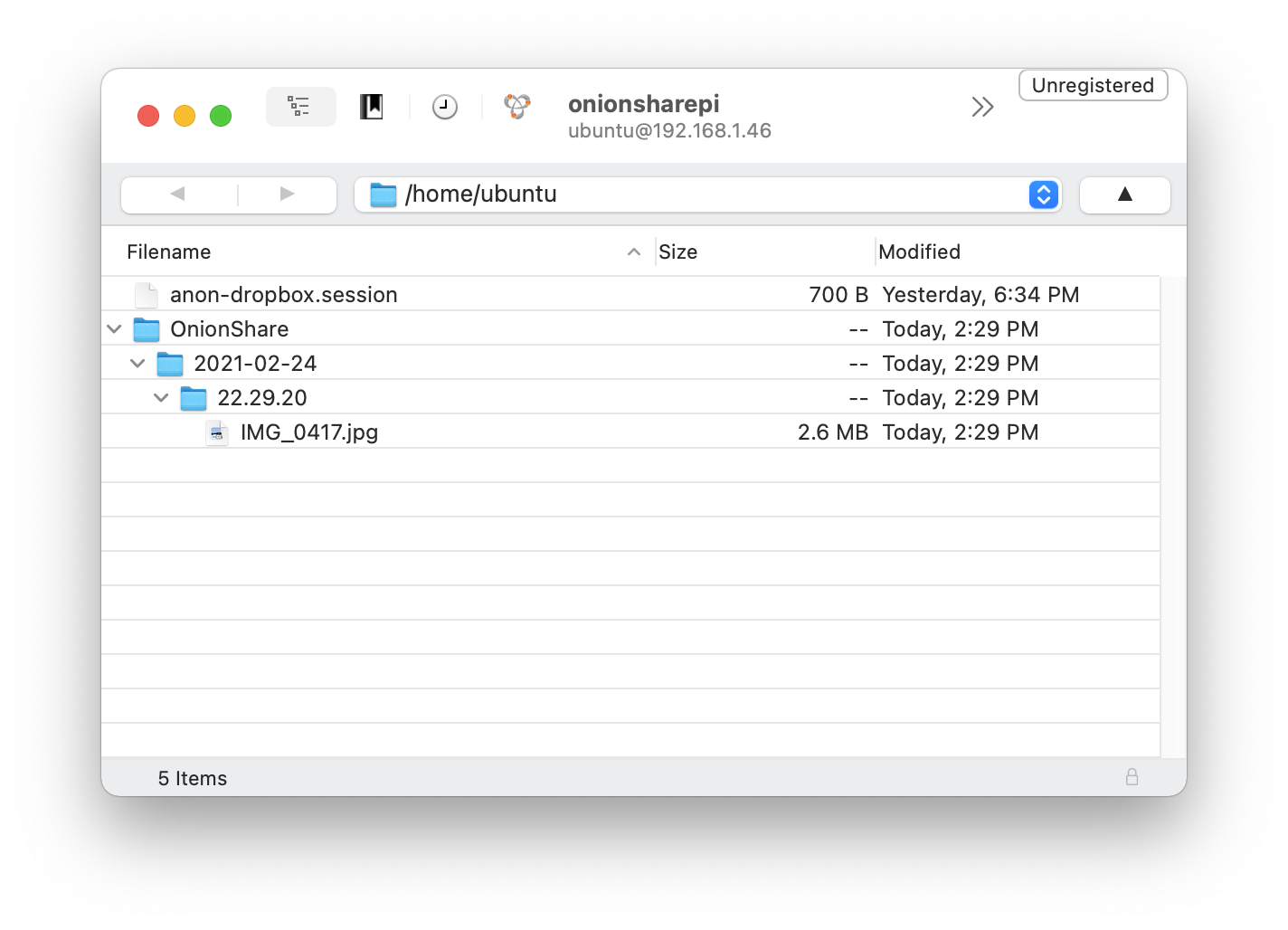
And finally, I can open IMG_0417.jpg and see what this image I uploaded was.

In Linux
In Ubuntu (or other distros that use nautilus as the file manager), I open the file manager, go to "Other Locations", and connect to the server sftp://ubuntu@192.168.1.46/.
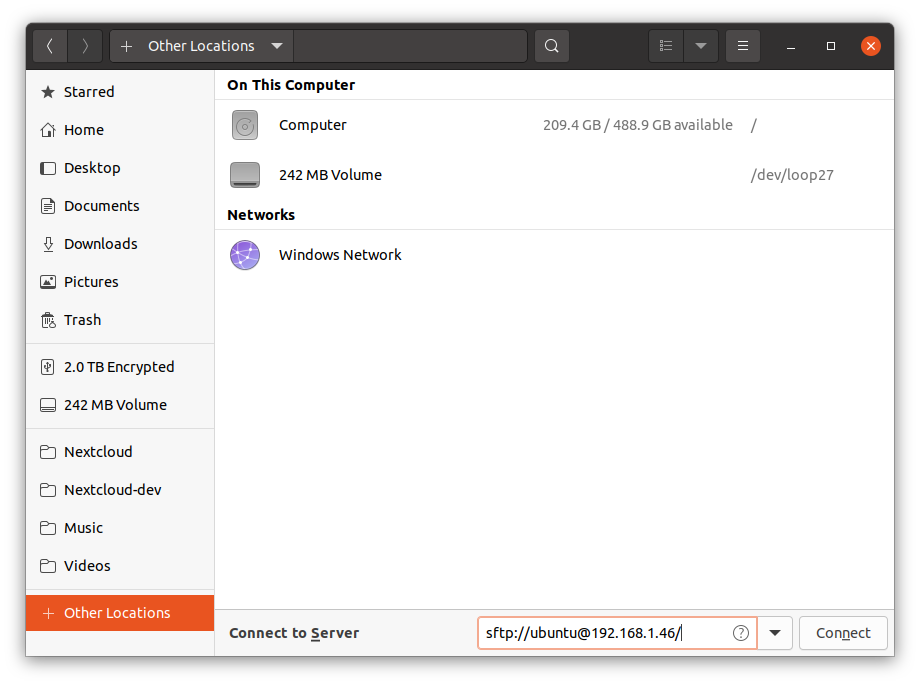
Now I have access to the files that get uploaded to my anonymous dropbox:
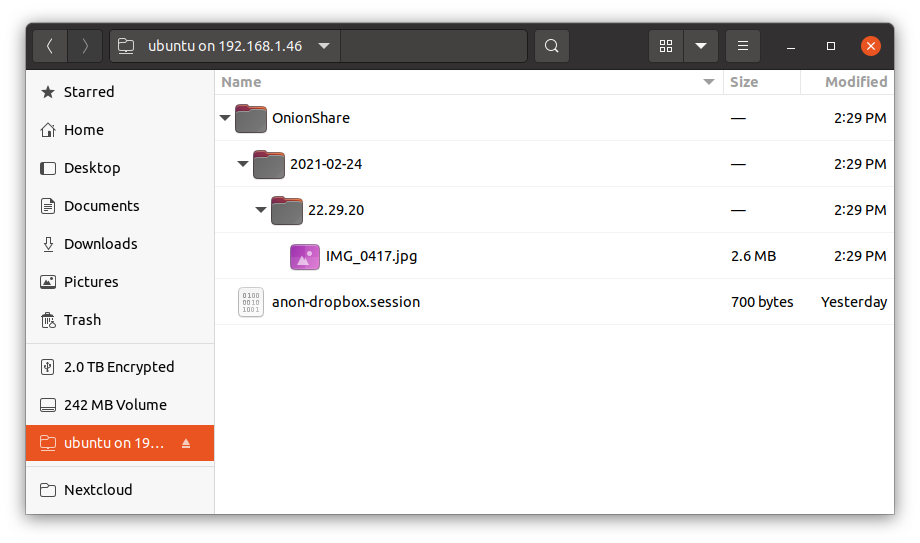
Make sure the anonymous dropbox is actually persistent
The command we used to start OnionShare in receive mode is:
onionshare-cli --receive --persistent ~/anon-dropbox.session --publicThis stores all the settings associated with this session, including the secret key required to get this same Tor onion address, in the file anon-dropbox.session.
If you quit OnionShare by pressing Ctrl-C, then run that same command over again (in the terminal press up arrow, then enter), it should start OnionShare again, and the URL should be exactly the same. This is important because if you ever have to quit OnionShare (like maybe you need to unplug the Raspberry Pi and plug it in somewhere else, forcing it to reboot), you'll be able to get your anonymous dropbox up and running again with the same address.
...and yup, I just confirmed persistence works on my end.
You may wish to copy and paste the contents of this file into a note field in your password manager, or otherwise make a secure backup of it. This way when you spill coffee all over your Raspberry Pi, you can get up and running again without too much trouble.
Run OnionShare in a screen session so you can close your terminal
So far this works great, but there's a big problem: When you SSH into a remote server (the Pi) and run a command (onionshare-cli), if you close your terminal, get disconnected from wifi, or otherwise end your SSH session, it will close onionshare-cli as well. Ideally you want it to just always be open and running in the background.
A simple way of doing this is using the program screen, a terminal multiplexer (you can also use tmux or whatever else you prefer). If OnionShare is running on your Raspberry Pi, quit it with Ctrl-C. Then from a terminal, install screen and download a simple .screenrc file so it will look a bit nicer:
sudo apt install -y screen
wget https://raw.githubusercontent.com/micahflee/dotfiles/master/.screenrcThen run screen:
screenYou should see a new bar at the bottom of the screen with 0 bash highlighted in yellow. This means you're inside a screen session now. (If you want to get nerdy, you may with to teach yourself more about using screen or similar terminal multiplexers.)
Now run onionshare-cli again:
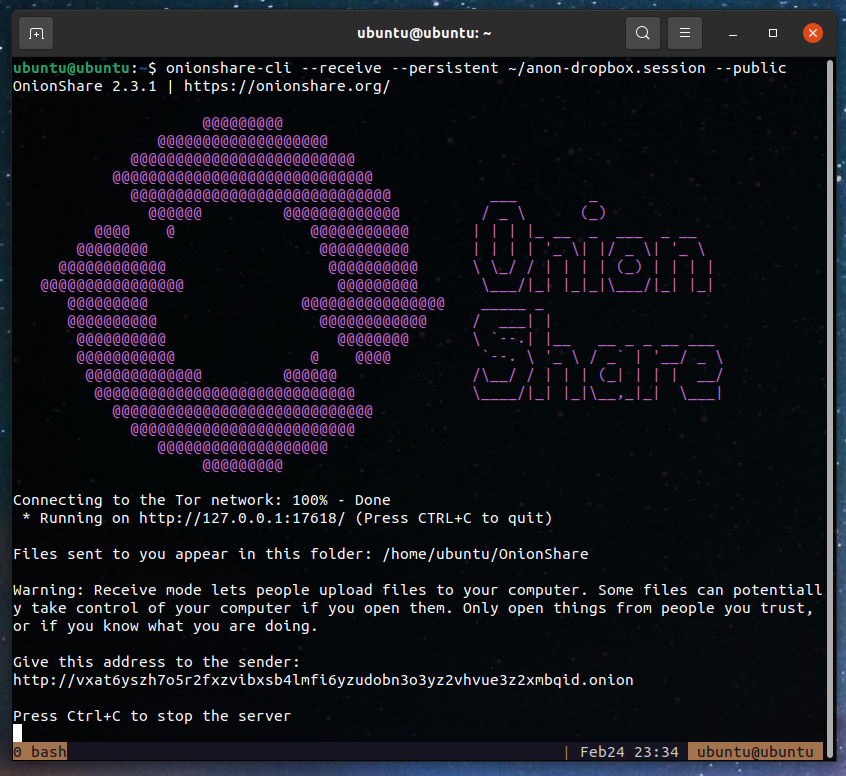
Now go ahead and completely close out of the terminal window, and make sure your you can still load your OnionShare address. It should load fine, because onionshare-cli should still be running on the Pi in your screen session.
Now let's get back in. Open a new terminal and SSH back into the Pi:
ssh ubuntu@192.168.1.46Once you're in, reconnect your screen session:
screen -xYou should see your OnionShare anonymous dropbox again.
Some final thoughts
After following this guide, you should have:
- A Raspberry Pi with Ubuntu Server 20.04 installed on it
- The ability to SSH into the server to remotely configure it
- An OnionShare anonymous dropbox running in a screen session
- The ability to access all the files that get uploaded to your anonymous dropbox on your normal computer
Congratulations! You're now equipped to accept leaks from the public. Just let people know that they can load your OnionShare address in Tor Browser to send you stuff anonymously. Here are a few things to keep in mind:
You can keep an eye on it by keeping a terminal open with the screen session attached to see when people access it, and regularly checking on the files that get uploaded.
Now that you're running a server, it's a good idea to regularly install updates so it doesn't get hacked, and keep an eye out for OnionShare updates as well (you'll be able to update onionshare-cli by running pip3 install --upgrade onionshare-cli). You might also want to do other things to harden your server like start using SSH keys instead of passwords or set up a firewall.
Your Raspberry Pi's hard drive is not encrypted, which means if someone can physically access your Pi, they can simply unplug the microSD card, plug it into their own computer, and copy all of the documents people have uploaded to you. The best solution is to add disk encryption to this setup (perhaps this will be the target of a future blog post -- if you're interested in that, post in the comments). But in the meantime, whenever someone sends you anything sensitive, you can download it to your computer and then delete it from the Raspberry Pi, and then securely erase the free space on the Pi's microSD card so that it can't be recovered.
To securely delete free space, install the secure-delete package:
sudo apt install secure-deleteAnd then run sfill to fill up all of the free space from zeros:
sudo sfill -v -l /In this command I'm using the flag -l which means "lessens the security. Only two passes are written: one mode with 0xff and a final mode with random values." -- though honestly I think this is fine for almost every use-case. This will take a very long time as it is, but if you leave off the -l it will take about 19 times longer, overwriting your free space 38 times instead of 2 times. (Run man sfill for more information.)
Warning: Receive mode lets people upload files to your computer. Some files can potentially take control of your computer if you open them. Only open things from people you trust, or if you know what you are doing.
This warning is prominently displayed in OnionShare, and I think it's important to point out again. Just like why you're instructed not to open sketchy email attachments, you shouldn't just blindly open documents that you receive from OnionShare. For a trivial example, if you use Windows someone can send you backdoor.exe, and if you open that file, they will have hacked you.
If you do get a document and you're worried it might hack you when you open it, here are a few strategies to try:
- If it's an office document, run it through Dangerzone first. This is another piece of software I wrote that turns office documents into PDFs that you can be confident won't hack you.
- If you're not concerned with sharing it with third parties:
- You can upload it to VirusTotal to get it scanned by dozens of anti-virus programs, which might help inform if you want to open it or not.
- You can also upload certain types of documents (including office docs, videos, and audio files) to Google Drive, and then view them in your web browser instead of programs like Word or VLC. If these documents would try to hack you, they'll instead try to hack some container running on Google's infrastructure, letting you view it safely.
- Set up a virtual machine, turn networking off, copy the document to your VM, and open it there. If it's malicious it will try to hack your VM instead of your host computer, and if it tries to phone home it will fail because your VM doesn't have networking.
Good luck, and I'd love to know if you're running an OnionShare anonymous dropbox of your own.
Oh and if you have any newsworthy leaks, feel free to send them my way: http://vxat6yszh7o5r2fxzvibxsb4lmfi6yzudobn3o3yz2vhvue3z2xmbqid.onion
