How the knock-off Signal app used by Trump officials got hacked in 20 minutes
Update May 21, 2025: I've written a new detailed analysis of the heap dump dataset itself: TeleMessage customers include DC Police, Andreessen Horowitz, JP Morgan, and hundreds more
Update May 26, 2025: I've published the source code for TeleMessage Explorer: a new open source research tool
During the last few weeks I've been consumed with researching TeleMessage, the Israeli firm that makes TM SGNL, the insecure version of Signal that former national security advisor Mike Waltz was photographed using.
After writing a few posts about it, on May 3, an anonymous source told me that they had hacked TeleMessage, and they told me exactly how they did it. When Joseph Cox and I broke the news about the hack for 404 Media, we didn't include any of the juicy details because it would be so trivial for anyone on the internet to reproduce it. Since then, TeleMessage has taken down their service, so this isn't a risk anymore.
Today, I wrote an article for WIRED (my first byline there!) that describes, in detail, exactly how TeleMessage got hacked in "about 15-20 minutes," according to my source. From my article:
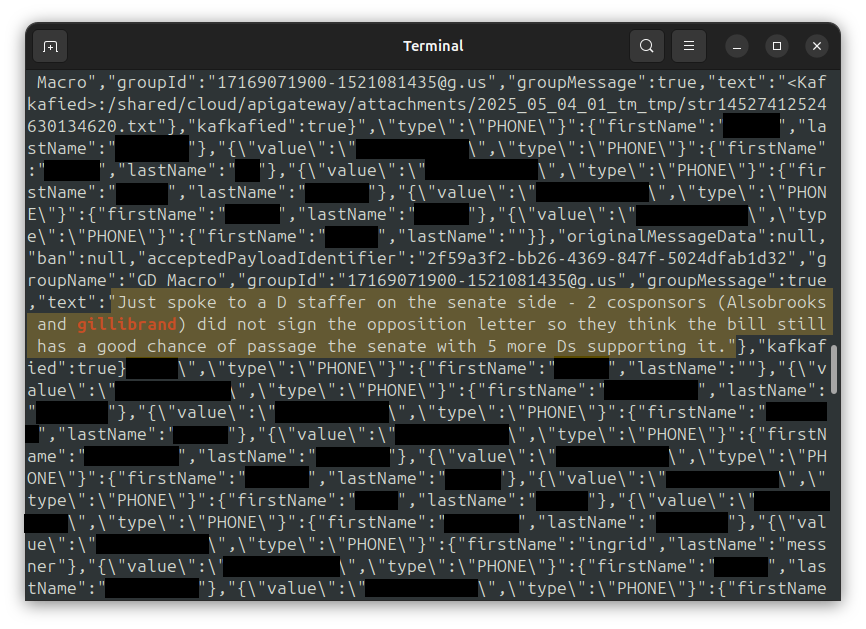
“I first looked at the admin panel secure.telemessage.com and noticed that they were hashing passwords to MD5 on the client side, something that negates the security benefits of hashing passwords, as the hash effectively becomes the password,” the hacker said. (Hashing is a way of cryptographically obfuscating a password stored on a system, and MD5 is an inadequate version of the algorithms used to do so.) Drop Site News has since reported that it appears that this admin panel exposed email addresses, passwords, usernames, and phone numbers to the public.
The weak password hashing, and the fact that the TeleMessage site was programmed with JSP—an early 2000s-era technology for creating web apps in Java—gave the hacker “the impression that their security must be poor.” Hoping to find vulnerable JSP files, the hacker then used feroxbuster, a tool that can quickly find publicly available resources on a website, on secure.telemessage.com.
The hacker also used feroxbuster on archive.telemessage.com, another domain used by TeleMessage, which is where they discovered the vulnerable URL: archive.telemessage.com/management/heapdump. When they loaded this URL, the server responded with a Java heap dump, which is a roughly 150 MB file containing a snapshot of the server’s memory at the moment the URL was loaded.
