TM SGNL, the obscure unofficial Signal app Mike Waltz uses to text with Trump officials
Update May 4, 2025: Another followup, and a big one: The Signal Clone the Trump Admin Uses Was Hacked
Update May 6, 2025: I've written a new detailed analysis. The findings are based on the TM SGNL source code and are corroborated by the hacked data: Despite misleading marketing, Israeli company TeleMessage, used by Trump officials, can access plaintext chat logs
Update May 18, 2025: I described TeleMessage's trivial vulnerability in an article for WIRED: How the knock-off Signal app used by Trump officials got hacked in 20 minutes
Update May 19, 2025: Uh oh: DDoSecrets publishes 410 GB of heap dumps, hacked from TeleMessage's archive server
Update May 21, 2025: I've written a new detailed analysis of the heap dump dataset itself: TeleMessage customers include DC Police, Andreessen Horowitz, JP Morgan, and hundreds more
Update May 26, 2025: I've published the source code for TeleMessage Explorer: a new open source research tool
Yesterday, a Reuters photographer captured a photo of the freshly-ousted former National Security Advisor Mike Waltz checking his Signal messages during a Trump cabinet meeting. If you're not familiar with Waltz, he's most well known for inviting The Atlantic's editor-in-chief to secret Trump administration war crimes Signal group. They discussed, and executed, bombing an urban apartment building full of civilians to kill a single man.
404 Media journalist Joseph Cox published a story pointing out that Waltz was not using the official Signal app, but rather "an obscure and unofficial version of Signal that is designed to archive messages" called TM SGNL.

This app uses Signal's servers, making it possible for Waltz to send end-to-end encrypted messages to normal Signal users, like Jeffrey Goldberg from The Atlantic, for example. However unlike the Signal end of the encrypted conversation, the TM SGNL end automatically archives a copy of the plaintext messages (even ones with disappearing messages) somewhere else that may or may not be secure.
In a video the company published, they show Signal messages getting archived into a Gmail account.
I decided to look into this app. I discovered:
- The senior executives of the company behind TM SGNL appear to be Israeli, and the CEO's bio mentions his work with Israel Defense Forces' Intelligence unit.
- TM SGNL is most likely violating Signal's open source license, and the company's other apps are probably violating the proprietary licenses of other software like WhatsApp and WeChat.
- The Android and iOS versions of the app are not available for the public to download, and in fact practically the only way to get the app is if you're using a device enrolled in an MDM service that's tied to an Apple Business Manager or Google Enterprise account.
- I speculate about exactly how I think the Trump administration is using this (unapproved for classified info) app to discuss classified info, and how they are likely managing their fleet of iPhones.
- Finally, I share a PDF and a video I discovered that go into detail about, among other things, where the chat logs may be stored.
Before I get started, consider subscribing to get these posts emailed directly to your inbox. If you want to support my work, considering becoming a paid supporter.
The company behind TM SGNL
The TM SGNL app is part of a suite of apps by a company called TeleMessage, which is owned by Smarsh, a company that makes e-discovery software, which is basically software designed for police and lawyers and whatnot to search archives of data.
I haven't spent a lot of time looking into TeleMessage, but what I did find at a quick glance is that several of the executives on the teams page list Israeli universities in their bios, and the CEO, Guy Levit, says that, "From 1996 until 1999, Guy served as the head of the planning and development of one of the IDF’s Intelligence elite technical units."
How the app probably works
Based on the photo of Waltz's screen, TM SGNL is most likely a version of Signal that is slightly modified. The app name is changed from "Signal" to "TM SGNL" (which is why Walt'z screen says, "Verify your TM SGNL PIN" instead of "Verify your Signal PIN").
And there is most likely an additional piece of code that gets executed whenever a message is sent or received which forwards the plaintext version of that message to the "corporate archive," as the company calls it.
TM SGNL might be violating Signal's open source licenses
Signal is open source. Here's the Signal-iOS code and here's the Signal-Android code. Because the code is available, creating an app like TM SGNL would actually be pretty easy to do.
Signal has done all of the hard work in making an end-to-end encryption messaging app. Signal also runs the server infrastructure. The TeleMessage devs simply have to clone the git repos of the client apps, figure out where to insert the archiving code, and make their own separate releases.
The Signal apps are licensed under the GNU Affero General Public License, a copyleft license that allows anyone to make modified versions (like TM SGNL) provided that they also use the same open source license. The license text says that when making modifications to the source code:
You must license the entire work, as a whole, under this License to anyone who comes into possession of a copy.
So, if someone has a copy of TM SGNL, they should be able to request that TeleMessage provide a copy of the source code, which should also be open source, and if TeleMessage does not comply they will be violating Signal's license – essentially, selling pirated software.
TeleMessage also publishes similar apps for WhatsApp, Telegram, and even WeChat, that probably work in similar ways. But because these apps are proprietary, I can't see any way that they're not violating the copyright on that app.
If I can find a copy of the TM SGNL app, I can not only request the source code, I could also try reverse engineering the app itself to see exactly how it differs from the official Signal app...
Trying to download the app
While I know Mike Waltz is using an iPhone, I'd actually prefer to get my hands on the Android version of TM SGNL simply because it's easier to crack open and look at its insides. But I'd settle for the iPhone version.
On the downloads page, TeleMessage lists two ways to install TM SGNL for Android and three ways to install it for iPhone.
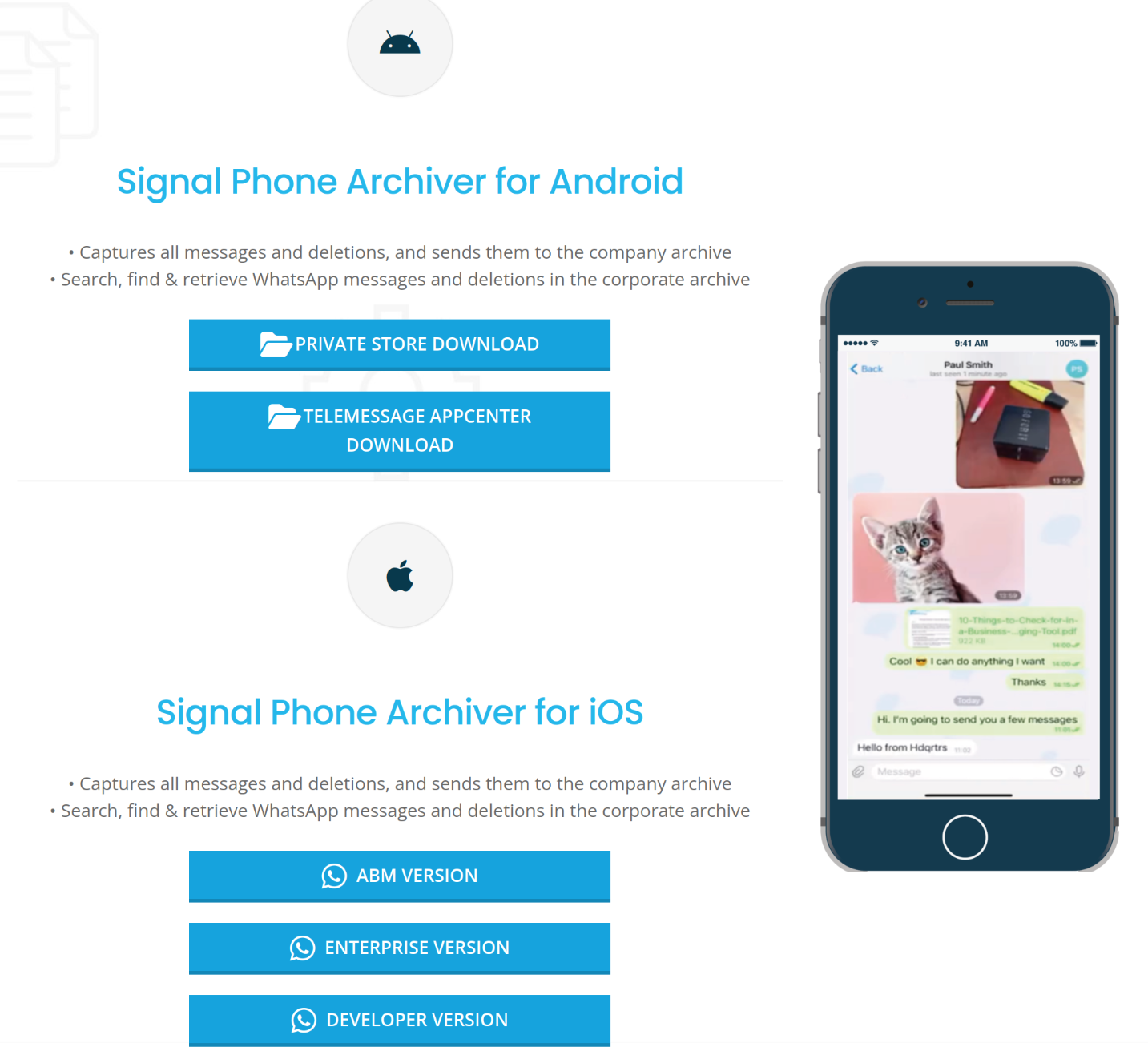
TeleMessage doesn't publicly distribute these apps in the Android Play Store or the iPhone App Store. So it's not as easy is just going and installing the app.
Android
The Private Store Download button links to documentation for allowing members of a Google Enterprise organization to download the app from Google's Private Store.
Basically, if your company uses Google Enterprise for device management, and your employees use Android devices, you can get TM SGNL added to a private part of the Play Store for your employees to download.
The instructions say to, "Copy your company’s Organization ID and email it to your TeleMessage project / account manager." This means that someone at TeleMessage needs to allow your organization to access the app. So, it looks like I'm not going to find a public download here.
The TeleMessage AppCenter Download button links just redirects back to the downloads page, so it doesn't actually work.
No luck. Let's try the iPhone version.
iOS
The ABM Version button links to docs explaining how companies can distribute apps to their staff using the Apple Business Manager.
Just like with Google Enterprise, if you want to give your employees access to the TM SGNL iPhone app, you need to share your ABM organization ID with TeleMessage, and then your account will gain access to a custom app which you can deploy to your employees. I'm not going to find a public download link here.
The Enterprise Version and Developer Version buttons link to docs explaining how to distribute the iOS app using either the Apple Developer Enterprise Program (used by big businesses to distribute custom or proprietary apps to their staff) or the Apple Developer Program (used by anyone who develops Mac or iOS apps – I have one of these accounts). In both of these options, the instructions include giving a TeleMessage account permissions in your Apple Developer account, allowing them to build and deploy versions of TM SNGL into your account. I won't find a public download link here.
Microsoft App Center
I had exhausted all of the options on the downloads page, but there was one more way to maybe get my hands on a copy of the app.
The TeleMessage website is incredibly sloppy. iOS links bring you to Android docs. A lot of the content seems to be old and out of date, but still public. Part of the sloppyness includes this page, called "Signal Capture Android Installation / Upgrade." I decided to use this sloppyness to my advantage.
This page instructs the user to:
- Allow installing apps from unknown sources. By default in Android, users can only install apps from the Play Store. By digging into the settings, you can allow installing apps from other app stores (like F-Droid), or by downloading APKs from websites.
- From your Android device, navigate to
https://www.telemessage.com/installsgapctrandroidand download and install the APK for TM SGNL.
This looked promising. In order to run this in Android, I installed Android Studio and spun up an Android emulator to load this URL in, but unfortunately it didn't work.
The URL https://www.telemessage.com/installsgapctrandroid redirects to https://install.appcenter.ms/users/tmwhatsapp/apps/telemessage-signal-android/distribution_groups/external, which should have allowed me to download the APK. But when I loaded it, I got this error message:
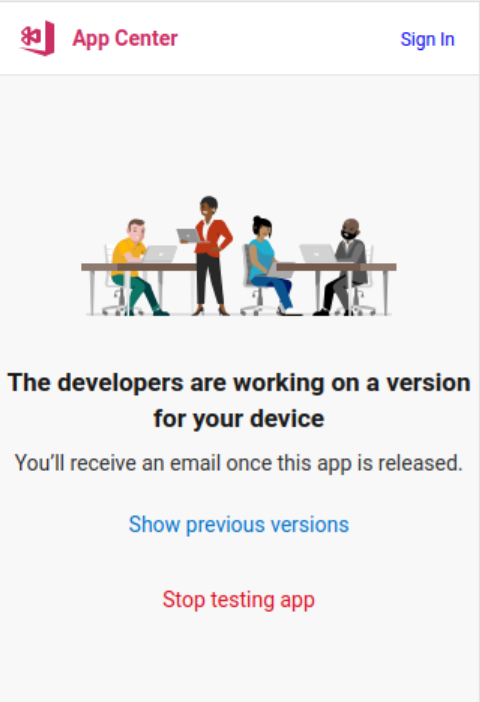
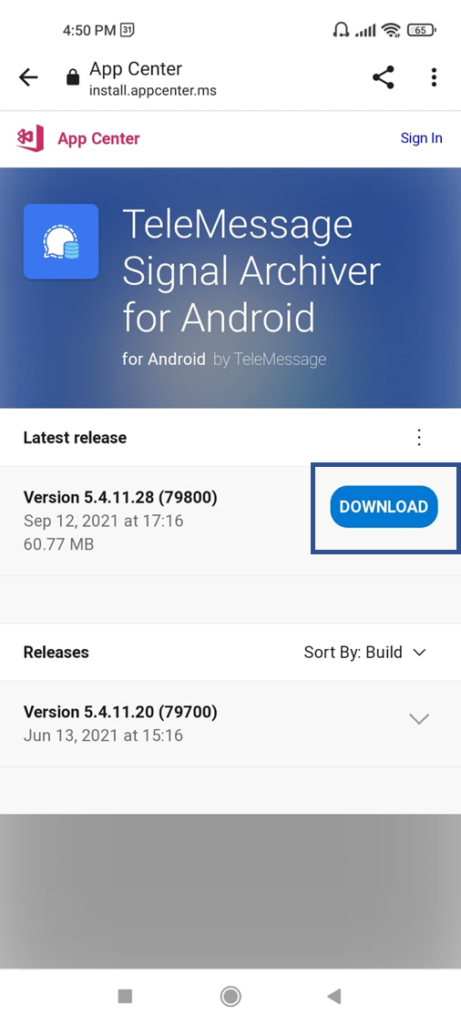
According to the docs, it should look like this:
To investigate further, I spun up Burp Suite – excellent software that allows you to inspect all of the HTTP requests a browser is making – and loaded the App Center URL.
Using Burp Suite, I discovered that the browser loads /api/v0.1/apps/tmwhatsapp/telemessage-signal-android/distribution_groups/external/public_releases, which return a JSON object containing a list of TM SGNL versions:
[
{
"id": 20,
"short_version": "7.36.2.10",
"version": "152900",
"origin": "appcenter",
"uploaded_at": "2025-03-16T15:42:35.547Z",
"mandatory_update": false,
"enabled": true,
"is_external_build": false
},
{
"id": 19,
"short_version": "7.27.1.7",
"version": "149800",
"origin": "appcenter",
"uploaded_at": "2024-12-26T07:38:42.175Z",
"mandatory_update": false,
"enabled": true,
"is_external_build": false
},
{
"id": 18,
"short_version": "7.18.0.5",
"version": "146800",
"origin": "appcenter",
"uploaded_at": "2024-11-25T13:00:26.541Z",
"mandatory_update": false,
"enabled": true,
"is_external_build": false
},Unfortunately this JSON object doesn't include URLs for APK files. I spent a bit of time digging into the now-defunct App Center docs, figuring out if there's a way to recover the APK URL. Alas, I came up short.
Mike Waltz, and presumably other senior Trump officials, are probably using managed iOS devices
As you can see in the photo, Mike Waltz uses an iPhone. And as I explored above, there are only a few ways to install TM SGNL onto iPhones. The simplest and most likely way is that his iPhone belongs to an Apple Business Manager account and is enrolled in MDM (remote management) service.
I have some experience running Apple Business Manager accounts myself. In order to create one, you need a legal entity that has a D-U-N-S number, which is a unique identifier for companies, managed by Dun & Broadstreet.
<speculation>
The following is all speculation, but here's what I think:
- The senior Trump people have some sort of legal entity. It might be the White House itself, or Trump's campaign organization, or something else, who knows.
- They have an Apple Business Manager account and are using an MDM service to remotely manage Apple devices. This central server is able to enforce settings, install apps, remotely lock or wipe devices, etc. The admin who runs the MDM service (as well as its hosting provider) has a lot of control over these devices. If I were foreign intelligence, this would be a primary target for me.
- The high level fascists in Trump's government, like Mike Waltz, Pete Hegseth, JD Vance, Tulsi Gabbard, etc., all have iPhones that are managed by this MDM service. They all use TM SGNL, which was automatically deployed to their devices via the MDM service.
- TM SGNL is configured on their devices to archive all messages (whether or not they automatically delete) to some central location. Knowing the level of incompetence and disregard for protecting classified information, my guess is it's storing the data in a public cloud provider like AWS or Azure, or in an email provider like Google or Microsoft. If I were foreign intelligence, this also be a primary target. People who hack this company, or malicious employees, can probably access all of these logs that are full of classified conversations.
</speculation>
Detailed documentation and a video for TM SGNL
If you click around through the sloppy TeleMessage website enough, you'll see plenty of links to URLs at https://docs.smarsh.com that say they contain up-to-date documentation. Clicking these leads you to a login page, so these docs aren't public.
However, I found this page which also links to a PDF version of the docs. I grabbed it before it's gone. Here is the 78 page PDF, with detailed documentation for TM SGNL, also known as Signal Capture:
Here's a brief tour of this document.
Where chat logs are stored
The docs start with showing admins for an organization how to login to the Admin Portal, which is hosted at https://secure.telemessage.com.
After logging in as an admin, the next step is to assign users to archive plans that include a source (an app like TM SGNL) and a storage destination "such as Microsoft 365, SMTP, and SFTP."
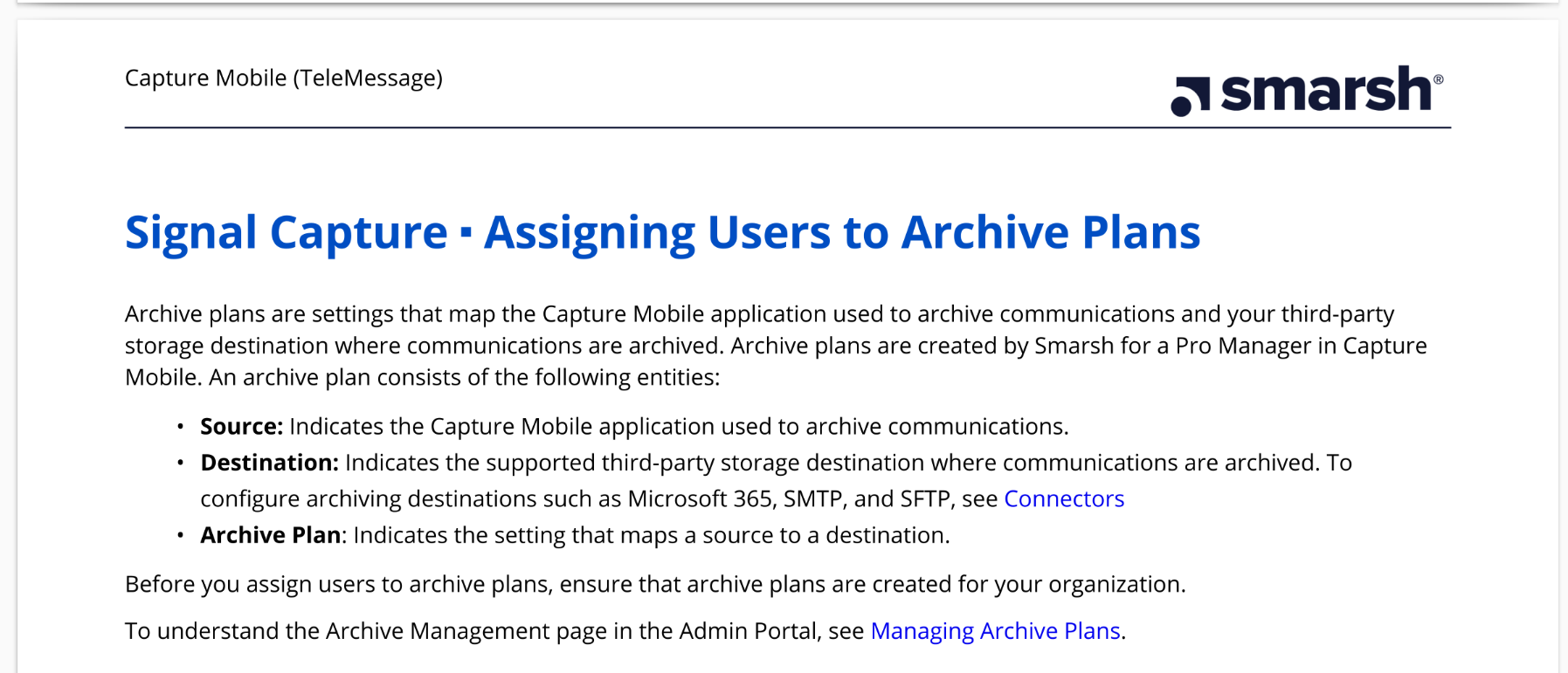
This gives a hint at the places where the classified Signal logs from senior Trump officials are likely stored. Microsoft 365 is Microsoft's suite of business services, and my guess is this refers to an Outlook email address. SMTP is an email protocol, meaning you can use any arbitrary email provider. And SFTP is a file transfer protocol, meaning you can store chat logs on arbitrary file servers.
The document includes a link to Connectors for more information, but unfortunately that links to a document behind a login page, so it's not public. This is all of the info I could find about where the chat logs are ultimately stored.
Assigning users to archive plans
The docs go on to explain how admins can assign different users (you know, people like Mike Waltz, Pete Hegseth, and Tulsi Gabbard) to archive plans. And this section even links to a publicly available (at least for now) video.
Here's a copy of the video, in case it disappears from where it's currently hosted:
Admin Portal - Adding a removing users from Archive Plans
While watching the video I noticed that, in addition to Signal, sources also include WhatsApp, Telegram, and even WeChat, which is the most popular messaging platform in China.
The destination for all archive plans in their test system is "Generic SMTP Archive," which really leads me to believe that most organizations will store archived data on an email server. This makes sense anyway, since email software has built-in features needed to search and investigate chat logs: support for threads that can contain two or more people, attachments, and robust search.
The narrator also mentions that Signal requires additional onboarding:
In the event that you have Signal or WeChat, there is some additional provisioning that is required from the Smarsh support side. So if you're going to be adding or removing users from Signal or WeChat, you will most likely need to be contacting Smarsh support to have the additional provisioning done on the backend.
Signal users using iOS devices will need to be specifically provisioned by Smarsh support. And WeChat, all users that are going to be utilizing WeChat will have to be provisioned on the backend by support.
How the TM SGNL app is distributed for Android and iOS
In the "Distributing the Android Signal Application" section, the docs make it clear that only Google Enterprise Private Store is supported. There's a note pointing out that distributing the app via App Center is officially deprecated.

The "Distributing the iOS Signal Application" section is even more illuminating. It lists two methods, using Apple Business Manager (which I described above), and also an "unlisted app," which I'll talk about more below.
TeleMessage distributes the TM SGNL app directly in the App Store, but as an unlisted app. This means you can't find it by searching the App Store. You need the actual URL of the unlisted app in order to install it. The docs say:
Signal Capture for iOS is published as an unlisted app in the App Store. You will receive a Welcome email from Smarsh with a direct link to the unlisted app. You must open this link in your iPhone device.
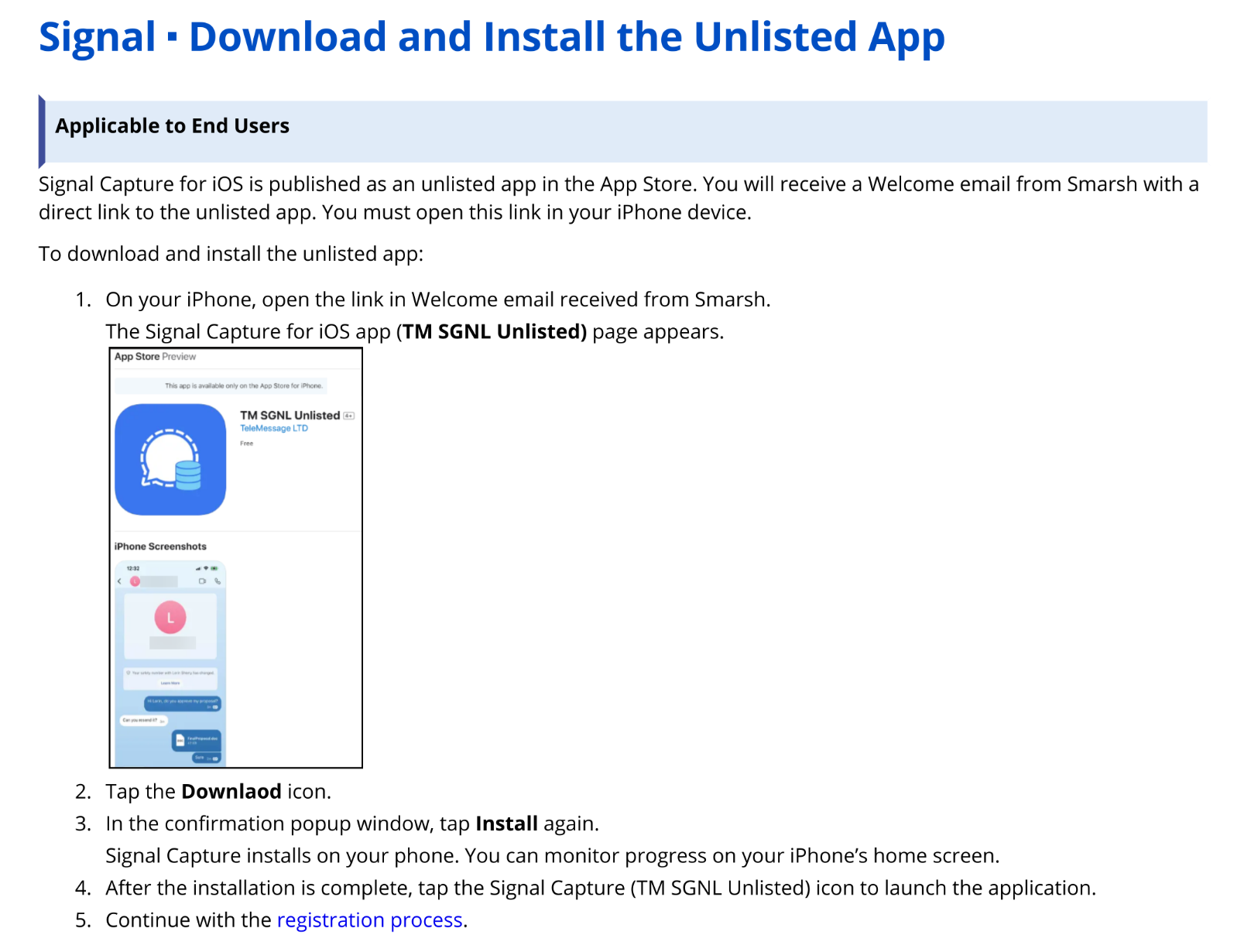
I don't have any way of learning the URL of this unlisted app. But if you happen to know it, please let me know.
That's it for now!
If you found this interesting, subscribe to get these posts emailed directly to your inbox. If you want to support my work, considering becoming a paid supporter.
