Hunting street-level cell phone surveillance with Rayhunter

Things are scary in the US right now. ICE is disappearing students for protesting genocide and kidnapping innocent people off the streets to enslave in El Salvador. All over the country, people are taking to the streets every week to protest oligarchy, and fascist counter-protesters are starting to show up at them. The police, particularly immigration police, are emboldened. Meanwhile, Trump is crashing the economy.
It feels like now is a great time to protect our communities by doing some countersurveillance of our own. So I was excited to read about EFF's new open source tool for detecting cellular spying called Rayhunter. Rayhunter is firmware that can be installed on a cheap WiFi hotspot that can detect cell-site simulators – also called IMSI catchers or Stingrays.
I bought a hotspot of my own to install Rayhunter on. Here's my experience with setting it up, and how you can detect these attacks yourself.
What's a cell-site simulator?
Cell-site simulators are devices used by police (and maybe others too, who knows) to indiscriminately spy on all cell phones present at a specific physical location, like a protest. Cell-site simulators, which are typically deployed in a vehicle, pretend to be legitimate cell phone towers, tricking nearby phones into connecting to them instead of actual towers. They work by basically doing a man-in-the-middle attack between cell phones and the cell tower that they should be communicating with.
They can see the unique IDs (called IMSIs) of all SIM cards in the area – allowing them to track which IMSIs show up to different protests over time, and potentially to identify individual activists. They can also potentially spy on any unencrypted phone calls and text messages (use Signal to avoid this!). And they can potentially spy on internet traffic too, but only if they can downgrade the mobile data to 2G (which is deprecated in the US), or if they have encryption keys for 3G or 4G from phone companies. It's not clear if local police have access to these, but maybe some agencies do.
The page on cell-site simulators in EFF's Street Level Surveillance field guide describes some of the times law enforcement agencies (including ICE) that have been caught using them in the past:
Law enforcement officers have used information from cell-site simulators to investigate major and minor crimes and civil offenses. Baltimore Police, for example, have used their devices for a wide variety of purposes, ranging from tracking a kidnapper to trying to locate a man who took his wife’s phone during an argument (and later returned it to her). In one case, Annapolis Police used a cell-site simulator to investigate a robbery involving $56 worth of submarine sandwiches and chicken wings. In Detroit, U.S. Immigration and Customs Enforcement used a cell-site simulator to locate and arrest an undocumented immigrant. In California, the San Bernardino county sheriff's office used their cell-site simulator over 300 times in a little over a year.
Police may have deployed cell-site simulators at protests. The Miami-Dade Police Department apparently first purchased a cell-site simulator in 2003 to surveil protestors at a Free Trade of the Americas Agreement conference. And it is suspected that they have been used more recently than that during protests against police violence in 2020.
Cell-site simulators are used by the FBI, DEA, NSA, Secret Service, and ICE, as well as the U.S. Army, Navy, Marine Corps, and National Guard. U.S. Marshals and the FBI have attached cell-site simulators to airplanes to track suspects, gathering massive amounts of data about many innocent people in the process. The Texas Observer also uncovered airborne cell-site simulators in use by the Texas National Guard. In 2023 it was revealed that ICE, DHS, and the Secret Service have all used cell-site simulators many times without following their own rules on deployment or getting a warrant.
I have no doubt that police under Trump right now are using cell-site simulators to spy on protesters, students, and immigrant communities. If you ever go to physical locations that might get targeted by the government, consider detecting if cell-site simulators are in use there!
There's no way to detect if you're being spied on with cell-site simulators using normal iPhone or Android phones. But if you're willing to spend about $30 and a bit of time, you can detect these attacks with Rayhunter!
What to buy
First, you need an Orbic RC400L mobile hotspot. EFF's blog post links to Amazon and eBay. I found a used one on eBay for $15.77 – but it ended up being closer to $23 after shipping.
Second, you need a SIM card. I don't fully understand how Rayhunter (or cell-site simulators) work. But from what I do understanding, it seems that you don't actually need to pay for phone service for your SIM. You just need a SIM plugged into your Orbic device.
Any SIM card should work. You can often find them at physical stores, by the racks where they sell gift cards. I checked a local CVS and Safeway and unfortunately they didn't have any. I heard Target sells them, but I'm boycotting Target right now. In the end, I ordered a Tello Mobile prepaid SIM card (with no service plan) from Amazon for $3. (I avoid buying stuff from Amazon, but I'm not currently boycotting it. Ugh, everything sucks.)
You'll also need a USB-C cable (my Orbic didn't come with one, but I had one laying around) and a computer running Linux, macOS, or, if you're willing to do extra work, Windows.
Installing Rayhunter
Once you get your Orbic and SIM card, flip your Orbic hotspot over and pry open the bottom-right corner to expose the battery. Remove the battery. Underneath it you'll find a slot for the SIM card. I found inserting it to be slightly tricky. You need to slide the metal to the right to unlock it, pull it open, slip the SIM card in, push it closed, and lock it again by sliding the metal to the left.

Plug in the battery and snap the back panel back on. Then, hold down the power button until the Orbic boots.
To install the Rayhunter firmware, follow the instructions in Rayhunter's README.md on GitHub.
Rayhunter doesn't support an automated install script for Windows. If you're using Windows, you'll need to follow the instructions to set up a development environment.
Basically, the steps for me were:
- Plug a USB-C cable from my Orbic to my computer.
- Download a file called
releases.tarand extract it. - Open a terminal and run
install.sh.
I first tried doing this on a laptop running Ubuntu 24.04. At first it seemed like it was working, but then it got stuck on a step where it was rebooting the Orbic and waiting for it to start again. I tried troubleshooting, and posted some comments on a GitHub issue.
But eventually, I decided to try the same process on a Mac, and it worked without a problem this time.
It's possible you might run into similar problems. If this happens to you, I recommend searching the issues on GitHub, or opening a new issue if you can't find one that matches your problem.
Using Rayhunter
Rayhunter keeps the same default user interface for the Orbic WiFi hotspot (and if you pay for service for your SIM card, you can even use it as a WiFi hotspot if you want), but it adds a thin green line at the top of the display.

If the line at the top turns red, then Rayhunter has found something suspicious. So far, I haven't seen it turn red, but I also haven't yet brought it to a protest.
If Rayhunter does find something suspicious, you can connect to the Orbic to download logs of whatever happened. Note that in EFF's blog post they say:
If you've received a Rayhunter warning and would like to help us with our research, please send your Rayhunter data captures (QMDL and PCAP logs) to us at our Signal username ElectronicFrontierFoundation.90 with the following information: capture date, capture location, device, device model, and Rayhunter version.
There are two ways to connect to your Orbic that are documented in the README.md. You can connect to the WiFi network the Orbic is running and load http://192.168.1.1:8080/, or you can plug it into your computer over USB and use the adb command to forward port 8080 over USB.
Since the WiFi way is simpler, that's what I'll do. On the Orbic, you can press the menu button a few times until it says "2.4GHz WIFI Info" (it maybe under 5GHz on yours, depending on settings), and then press the power button. It will then show you the name and password for the WiFi network, like this.

Next, connect your computer to this WiFi network.
Finally, load http://192.168.1.1:8080/ in a browser. It should look something like this:
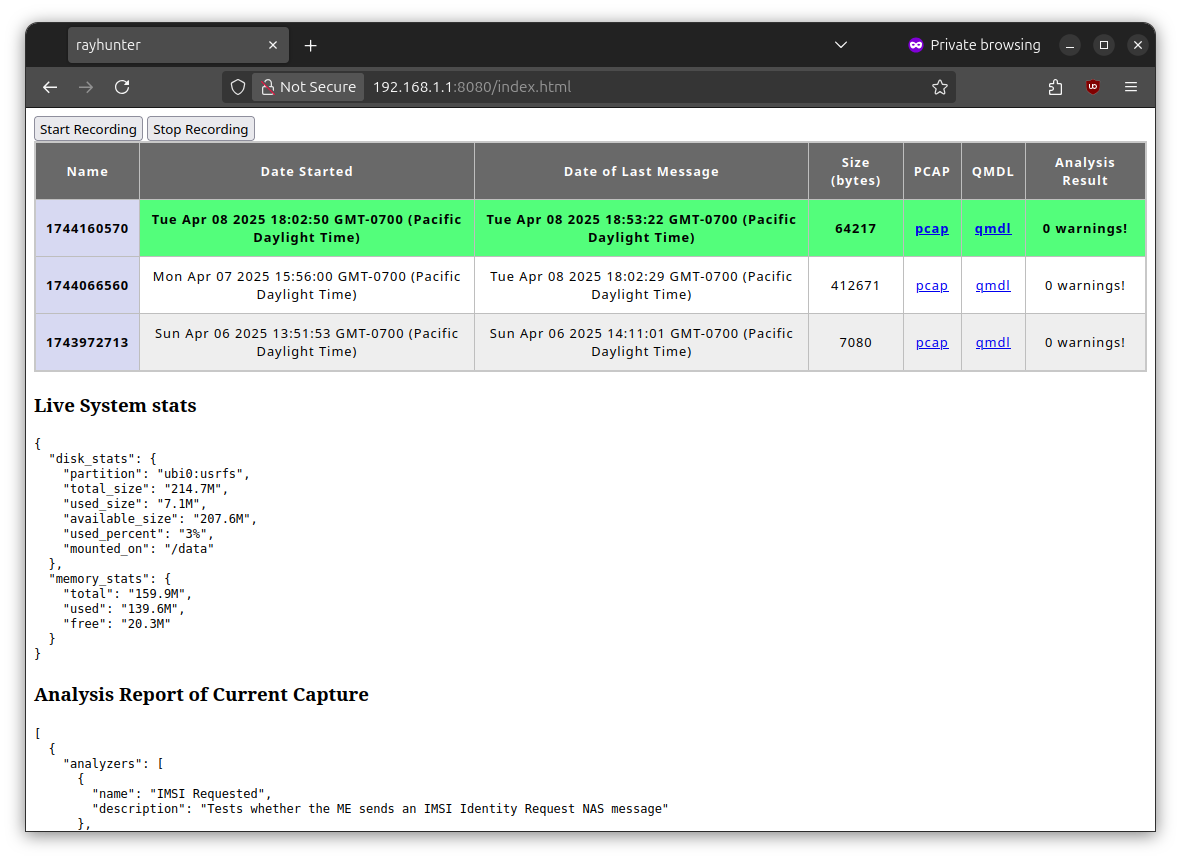
From here you can see information about what Rayhunter is collecting. You can download logs in PCAP or QMDL format, which are packet dumps. If a suspicious event was detected, these would contain the evidence.
Happy hunting!
If you're planning on getting an Orbic and hunting for cell-site simulators yourself, make sure to read the FAQ. I'll be bringing mine with me to protests, as well as anywhere else I think I'm likely to detect attacks. I'll report back if I find anything.
If you found this interesting, subscribe to get these posts emailed directly to your inbox. If you want to support my work, considering becoming a paid supporter.
