Here's the source code for the unofficial Signal app used by Trump officials
Update May 6, 2025: I've written a new detailed analysis. The findings are based on the TM SGNL source code and are corroborated by the hacked data: Despite misleading marketing, Israeli company TeleMessage, used by Trump officials, can access plaintext chat logs
Update May 18, 2025: I described TeleMessage's trivial vulnerability in an article for WIRED: How the knock-off Signal app used by Trump officials got hacked in 20 minutes
Update May 19, 2025: Uh oh: DDoSecrets publishes 410 GB of heap dumps, hacked from TeleMessage's archive server
Update May 21, 2025: I've written a new detailed analysis of the heap dump dataset itself: TeleMessage customers include DC Police, Andreessen Horowitz, JP Morgan, and hundreds more
Update May 26, 2025: I've published the source code for TeleMessage Explorer: a new open source research tool
Yesterday, I published an analysis of what I could publicly find about TM SGNL, the obscure and unofficial Signal app used by Mike Waltz, and presumably also by Pete Hegseth, JD Vance, Tulsi Gabbard, and other fascists in Trump's government. Afterwards, someone privately sent me the URL https://www.telemessage.com/wp-content/uploads/2024/12/Signal.zip.
I downloaded Signal.zip and was excited to see that it's the Android source code for the app! I immediately started digging in. Before the night was over, two different people also sent me this same URL, and cryptographer Matthew Green slyly tweeted it too.
I'm still analyzing it and omg, I'm excited to share my findings soon.
Meanwhile, people over on Mastodon have been discussing the TM SGNL app, and lj·rk made an incredibly find: public links on the TeleMessage website to the source code for not only the TM SGNL Android app, but the iOS app too.
- TM SGNL Archiver source for iOS:
https://telemessage.com/wp-content/uploads/2024/12/Signal-iOS-main.zip - TM SGNL Archiver source for Android:
https://www.telemessage.com/wp-content/uploads/2024/12/Signal.zip
The website, and the source code itself, also makes it clear that this code is licensed under GPLv3. This means that TeleMessage has granted me (and everyone else) the right to access the code, analyze it, modify it, and do whatever else we want with it, so long as we publish any derivative work under the same license.
Considering the incredibly newsworthiness of this – the most powerful officials in Trump's authoritarian government are using this (essentially backdoored) version of Signal to discuss classified information and plan war crimes – I decided to publish mirrors of this source code on GitHub to make it easy for anyone to access.
Here you go:
I've been spending my weekend so far analyzing the Android version. While I'm still working on a bigger report, I wanted to quickly share a few interesting things.
The Android source code includes a full .git folder, with a complete Git history and multiple branches and tags, all of which I have pushed to GitHub. We can see exactly who contributed what code. And while it's not easily viewable from the GitHub interface, if you clone the repo you can see their email addresses – moti@telemessage.com, shilo@telemessage.com, davidt@telemessage.com, etc.
Unfortunately the iOS version doesn't include a .git folder, so there's no Git history there. My mirror just has a single commit I created today.
The Git origin included in the Android code originally was: https://TMGitlab.telemessage.co.il/client/Android/signalarchiver.git. This looks like a private GitLab server (an open source self-hosted alternative to GitHub), hosted on a subdomain of telemessage.co.il, a domain with an Israeli TLD. This server is not accessible to the public internet, so probably their developers connect to a private network to gain access.
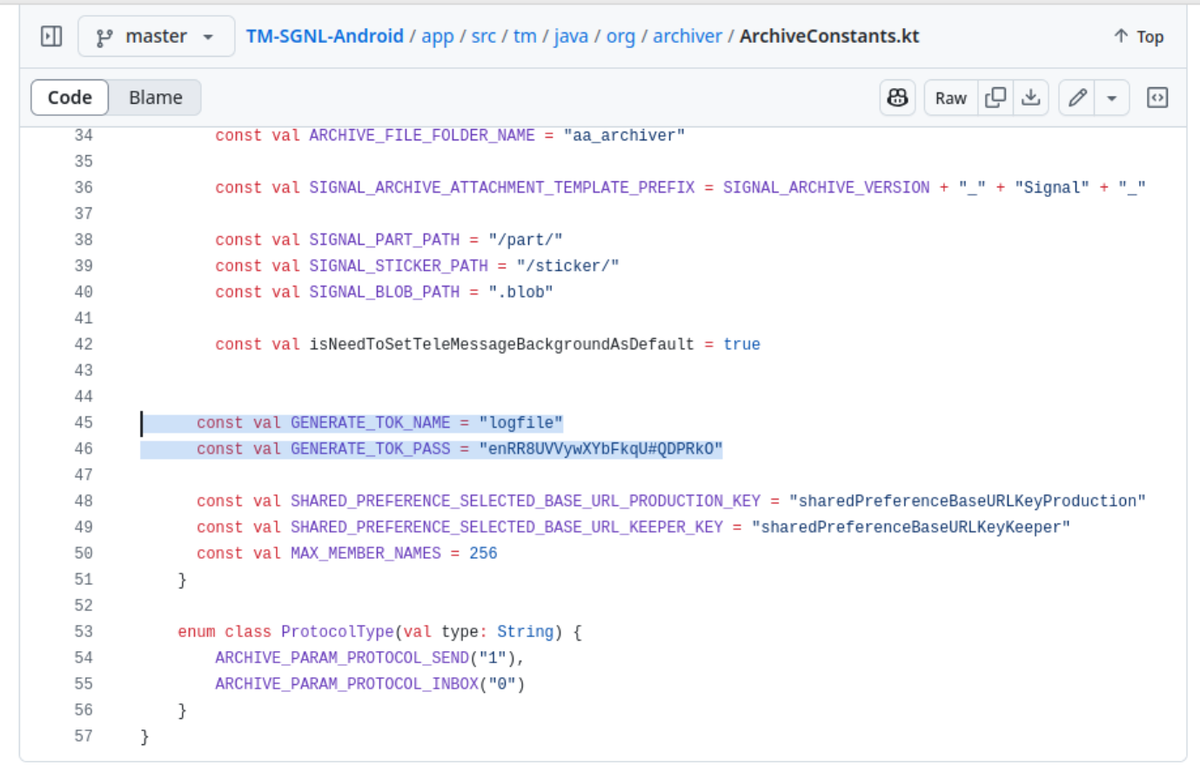
The source code contains hardcoded credentials and other vulnerabilities.
If you found this interesting, subscribe to get these posts emailed directly to your inbox. If you want to support my work, considering becoming a paid supporter.
