

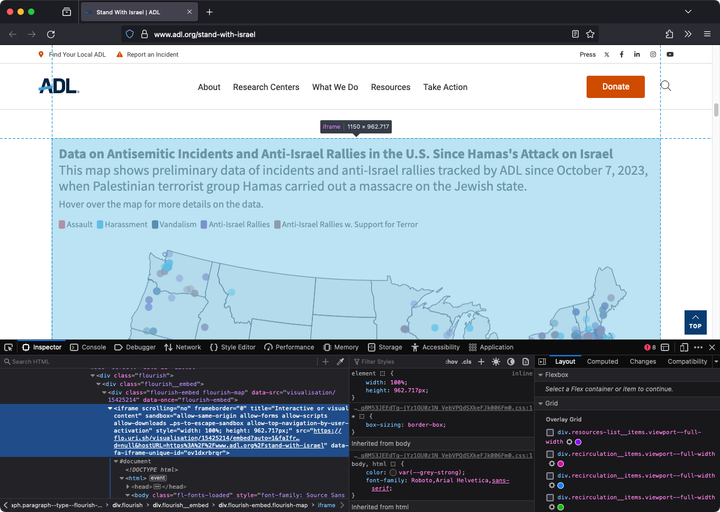
CASE STUDY: Extracting data from ADL's "Antisemitic Incidents and Anti-Israel Rallies" map
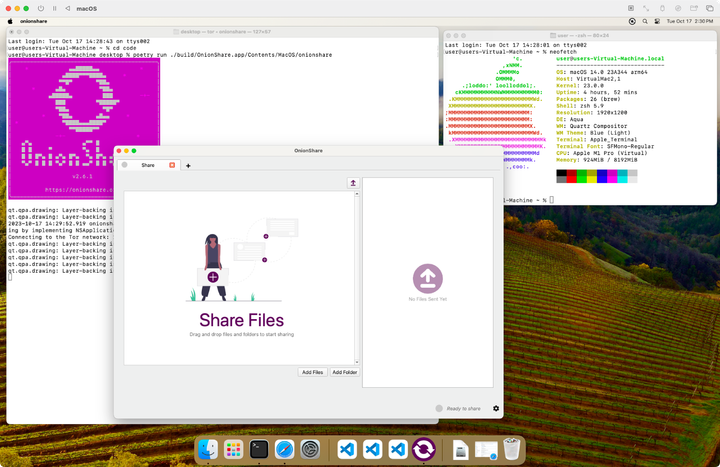
What goes into making an OnionShare release: Part 3

What goes into making an OnionShare release: Part 2

Hacks, Leaks, and Revelations: Pandemic Profiteers and COVID-19 Disinformation


