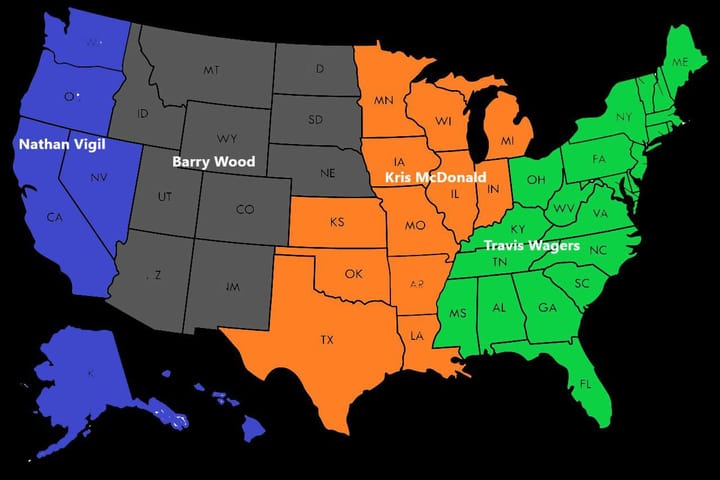

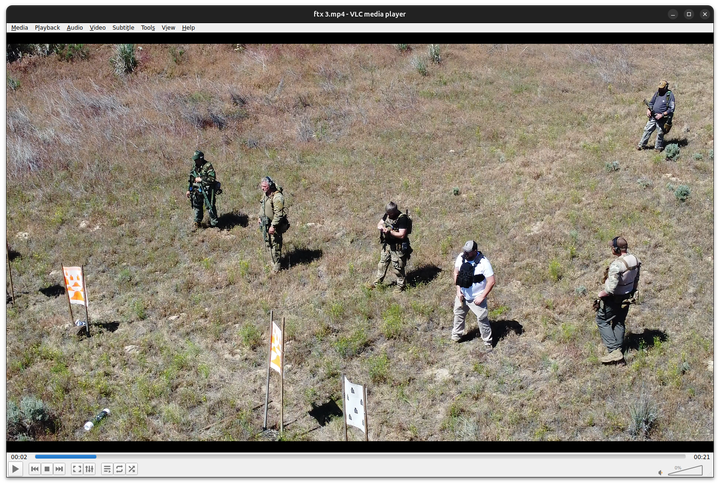
Exploring the Paramilitary Leaks

Fight fascism and Elon Musk by taking down Tesla

Grok will share detailed responses from X's API, but alas, it can't access DMs and likes

I just moved my website to Ghost! Get updates delivered to your inbox and support my work


